Showing posts with label virus. Show all posts
Showing posts with label virus. Show all posts
Monday, April 6, 2020
Amazon Prime member? WARNING!
I have an Amazon account AND an Amazon Prime membership.
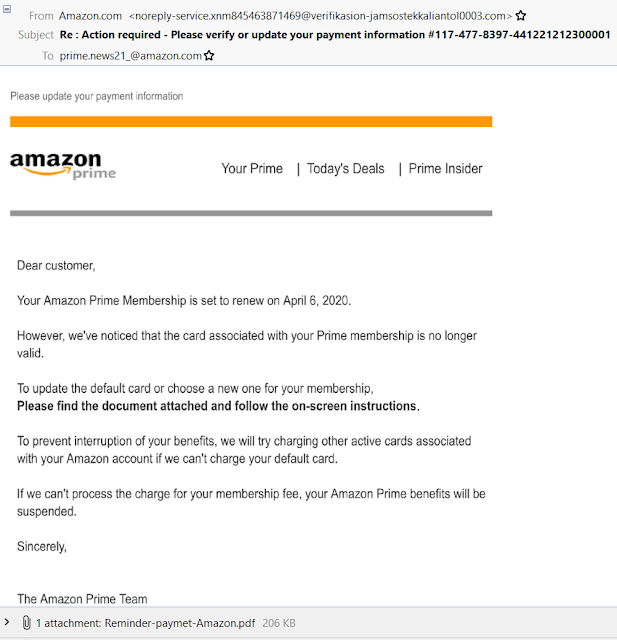
I received an email and I want to show it in a screen shot:
On first glance nothing really alarming, right?
BUT:
The sender email address (labeled From:) looks to me totally wacky and the Reply-To address (labeled To:) IMHO is equally unlikely.
The warning bells in my mind started to ring loud and clear.
My wife and I use the same Amazon account all the time and thus I know that the payment method is correct and that it works.
Even saving the attached PDF document to my computer and then scanning it with Malwarebytes did not show any alarms or warnings.
So I opened the file in my PDF reader to check it out in more detail.
The PDF document contains a link and a BIG button to supposedly go to Amazon's account and payment method web page.
BUT this is what the link and the button actually would have sent my web browser to:
https://t.umblr.com/redirect?z=https%3A%2F%2Fam1zn-updtaeinfmtaonsupdtee-verifyconfimationss76757855.com%2F%3Fsigninn-&t=NmVmZTU1YjdlNTBkODkzYjc0NTg1NzM0MTI2YWNhNWJkOGNiZGRjZSxjYTVkNGQyNzY5ZjI4OGQ2OGFiZjQ2ZDJmOTg3NjZlMTZkNTI5M2Y3
What a crazy nightmare - and for me a clear indicator that something was VERY WRONG!
I went to Amazon.com and checked in my account settings and voila, my Prime membership is paid for until September and the payment information is correct.
Naturally I will report this to Amazon.
MY conclusion as far it concerns you?
Be super vigilant, never trust an email and do NOT be complacent!
Yes, IMHO it is complacent to "just click" on the big button or the link in the PDF file rather than verifying the claim made in the PDF file independent of the email and it's attachment!
Stay safe, stay vigilant and pay attention to the details!
Monday, March 28, 2016
Ransomware - A Current Example
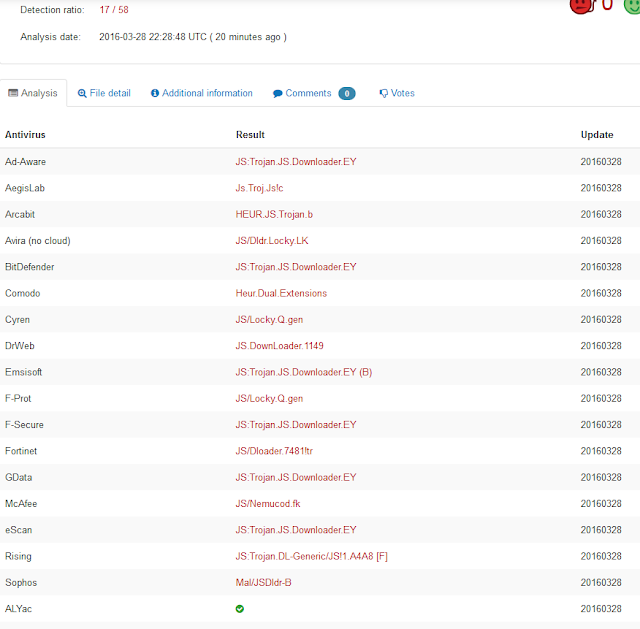
Please take a close look at this cut out grabbed diectly off my screen:
From the top the red frames are around:
- The virus infected scam email in the message list
- The totally unprofessionally empty subject line.
[Bulk] is from my ISP telling me that this email was sent from a server that is known to send out spam
FW: tells me that the email was forwarded - Addressing me with "ejheinze" shows that the sender does not even know my first name;
ejheinze is the part of my email address before the @ character - A totally unprofessional signature
- .zip is one of the potentially dangerous file types
- Hm, no subject and I don't know a Jodie M and Comcast in her email address? I have no business at all with Comcast.
- Unprofessional and bordering on rude.
- Totally unprofessional and in a primitive way impolite.
- From Comcast I would at least expect some sort of company logo or an avatar.
- I wonder what might be in there...
but with all the above I DO NOT CLICK on the attachment!
The rest was simple:
Delete the email which deletes the attachment as well.
Delete the file from the computer and
Empty Recycle Bin, just to be sure.
Remember: NEVER, EVER click on an email attachment unless you have verified it's legitimacy with the sender.
Stay safe.
Labels:
email,
general,
netiquette,
pup,
ransomware,
thunderbird,
virus,
Virustotal
Monday, March 21, 2016
New Dangers And Bad News
You may already have heard of ransomware, the newest trick of the bad guys to get at your money.
If you have not here is a VERY SHORT explanation: A ransomware virus encrypts all your data files, that is in effect makes them unusable and unreadable. After the encryption is done you have to pay money to the crooks do get instructions and a "decryption key"; if the instructions and the decryption key work correctly as they should you get your data back but sometimes it does not work. Your data is held for ransom, hence the name.
So far the highest amount reportedly paid by a large California based medical organization was 17 million dollars.
Very recently the web sites of a whole lot of well known and big organizations got abused to show advertisements infected with ransomware. Some of the affected web sites were:
- msn.com
- nytimes.com
- aol.com
- nfl.com
- theweathernetwork.com
- thehill.com
- zerohedge.com
I can not say it often and loud enough:
If you see advertisements on the Internet your web browser and thus your computer are NOT SAFE at all! Fire your current technician and call me or send me an email!When I leave a customer's house they ALL have a safely set up web browser that should not show ANY of these commercially distributed advertisements.
Stay safe.
Labels:
ad-blocker,
adblocker,
encryption,
general,
malvertisement,
malvertising,
ransomware,
virus,
warning
Tuesday, April 28, 2015
Bye bye Viruses, Hello Carelessness
It's almost like in the Everly Brothers song "Bye Bye Love" from 1957. They sang
Bye bye happiness, hello loneliness...
I am enticed to, no, don't be afraid, not sing but say
Bye bye viruses, hello carelessness...
In August 2014 I wrote in this blog the 2014 Update On Malicious Programs. Everything in this article is still valid today – which in the fast changing world of computers is astonishing all by itself. Self replicating viruses that "find and infect" our computers by their own accord have gone almost extinct.
What has massively changed though are the tricks and methods used by miscreants to foist their malicious junk software on our computers. It is so bad that I feel compelled to say
Do NOT click on any link in any email,
do NOT open any email attachment
and NEVER click in any advertisement.
do NOT open any email attachment
and NEVER click in any advertisement.
Does that sound extreme to you? Good, because it is extreme. We are in an extreme situation and it's getting worse so extreme measures seem appropriate.
In the meantime you have learned to immediately delete emails with an unfamiliar sender address. But what about the email from that buddy of yours who always sends all the jokes? My advice is to IGNORE it! Just hit the Delete button. If that email really was from him and if he were a nice guy he would have told you in the email why and what he sends there. If he does not have the decency to do that you better err on the side of caution and delete that email; you may “miss” a joke but what is that compared to $100 or $200 cost for a good clean-up job?
Another way how modern malware (called PuPs) is distributed are dirty tricks pulled on us when we apply required updates. Even big, well known companies participate in these schemes; names that come to mind as examples are Oracle, Norton, McAfee and Adobe. Some visual examples are here.
And don't get me going on advertisements. Listen up:
If you see advertisements on your computer screen then you computer most likely already is compromised. Get it cleaned up!
And then the sneaky methods that well known download web sites like Download.com, Cnet.com and other use. You want to download that nice free little program and what they give you is a specially crafted downloader program that in turn is supposed to download the program you actually want. But what you get are one or several PuPs and then the program you really wanted.
The only method to help here is to watch for the tricks, traps and deceptions.
In July 2013 I published my 10 Commandments Of Safe Computing. To heed the first of these has become more important than ever before; it reads:
Thou shalt read and think(!) before you click.
Be vigilant, pay attention to details and always remember: If it sounds too good to be true it usually is not true; especially in this day and age on the Internet.
As usual I welcome suggestions and comments right here in the blog.
Click here for a categorized Table Of Contents.
As usual I welcome suggestions and comments right here in the blog.
Click here for a categorized Table Of Contents.
Monday, September 1, 2014
Details on CryptoWall
This article assumes that you are familiar with my previous article CryptoLocker - Revisited.
Detailed information was released about CryptoWall, one of the CryptoLocker variants.
Between mid-March and late August CryptoWall infected almost 625,000 systems; on these systems it encrypted more than 5.25 billion files.
The US seems to have the most CryptoWall infections: 253,521 (or about 40 percent), followed by Vietnam with 66,590 infections, the U.K. with 40,258, Canada with 32,579 and India with 22,582.
The US likely got targeted more often because CryptoWall's got distributed through spam emails sent from the Cutwail botnet which targets English language computer users.
Researchers collected data directly from CryptoWall's payment server such as the exact number of paying victims and the amount of payments. Of nearly 625,000 infections and over about six months 1,683 victims (0.27%) paid the ransom for a total of $1,101,900.
CryptoWall seems to have a home-made problem by accepting payment of ransom by Bitcoin only. Many average computer users will have problems paying with Bitcoin and reseachers assume that this is part of the reason that only 0.27% of CryptoWall's victims paid compared to 1.3% of CryptoLocker victims; CryptoLocker allowed payment by MoneyPak as well.
As sad as it is, these numbers clearly show that cyber crime pays.
As usual I welcome suggestions and comments right here in the blog.
Click here for a categorized Table Of Contents.
Labels:
clean-up,
cleanup,
crapware,
CryptoLocker,
cryptowall,
email,
fireeye,
fox-it,
general,
malware,
privacy,
ransomware,
recommended,
security,
support,
Trojan,
virus,
warning
Tuesday, August 26, 2014
CryptoLocker - Revisited
In December 2012 I wrote for the first time about the back then new relatively virus CryptoLocker.
In October 2013 I wrote again about new variants of this virus. Now I have new information that warrants to visit CryptoLocker again.
This family of viruses is by now one of the most destructive threats I have seen. Much of the news regarding CryptoLocker is rather negative but there is at least a bit of positive news as well.
CryptoLocker has evolved
Very shortly after the original CryptoLocker had appeared the first variant was discovered; on first glance it appeared to be similar to the original version. It almost was a look-alike, the method of infection was the same, the encryption seemed the same and the message on the infected computer's screen was very much like the original's. There were only two obvious differences: The original CryptoLocker demanded $100 for information to decrypt the user's files and it offered two payment methods (MoneyPak or Bitcoin); the “look alike” demanded $300 and accepted Bitcoin only.
Time consuming and detailed analysis uncovered significant internal differences. Specialists found that the second version most likely was written by a different programmer or even programming team. It was written in a different programming language and many other internal differences were discovered as well.
In the meantime we know of at least six other virus programs that work similar to CryptoLocker. They are called “encrypting ransom ware” (in the following ERW), they are actively distributed, modified and improved. Most likely they were created and are being run by different groups of malware creators and distributors. Some names I have run across:
- CryptoLocker (the original)
- CryptoLocker 2 (the first imitator referenced above, my naming))
- Critroni
- CryptoDefense
- CryptorBit
- CryptoWall (see this new article for details)
- CTB Locker
- PrisonLocker or PowerLocker
- TorLocker
How these infections spread
Many infections happen when the user attempts to opens an e-mail attachment that then in turn launches the ERW. By now almost any file type can be abused in this way; you just can't trust so called “safe” file types any longer.
Over time I have received many emails about supposedly failed deliveries of goods. Some of these emails were made professionally and looked at first glance almost authentic. It made no difference whether the email seemed to be from DHL, FedEx, UPS or the US Postal Service; there always seemed to be some legitimate sounding reason to open the attachment.
In all cases attention to detail and applied common sense protected my computer better than any security program could have done; I simply avoided that one fatal click to open an attachment.
Another increasingly often encountered way for ERWs to spread are “drive-by downloads”. They come from compromised websites and compromised web servers. These sophisticated attacks take advantage of known vulnerabilities in almost ubiquitous software like Windows, Adobe Flash, Adobe Reader, Java and so on. Since these vulnerabilities are known there is only very little excuse to get caught by a drive-by download. To get the computer infected by a drive-by download is very unlikely if the user keeps all software up to date.
Protection?
On the positive side we have to my knowledge three options, some free and some with premium versions for a charge. These programs do not interfere in or conflict with common anti virus or security software. I warn against running any two of these programs concurrently due to the likelihood of conflicts with each other.
1. CryptoPrevent
2. MalwareBytes Anti-Exploit
3. HitmanPro Alert with CryptoGuard
If you are interested to learn more please follow the links.
To make it perfectly clear: I am convinced that the best protection is our own attention to detail, caution and applied common sense. No software in the world can replace our watchfulness!
ERWs on non-Windows computers
To make a bad situation even worse there are reports of ERWs on other, non-Windows platforms like tablets and smart phones with the Android operating system. There was talk about a popular NAS system (Network Attached Storage) being targeted as well. Only Apple systems seem to be not affected, so far at least; as we all know that can change any moment.
A bit of good news
Fairly recently, I believe it was in early August 2014, two software companies announced that they have jointly developed a method to decrypt at least some of the files that were encrypted by the original CryptoLocker. The companies and their web sites are The companies offer their program free of charge to people who still have files encrypted by the original version of CryptoLocker who wants to attempt to recover them.
The companies are FireEye (www.fireeye.com) and Fox-IT (www.fox-it.com). These companies apparently did not crack the encryption, they gained access to some of the command and control servers where some private keys were stored that the original CryptoLocker virus had used.
Much detailed sleuthing, dis-assembling, re-engineering and analysis of the original virus enabled them to write a program called DecryptCryptoLocker that can decrypt affected files when the were encrypted using any of the recovered private keys. At https://www.decryptcryptolocker.com/ you can read how this works. There is a decent chance that this program will recover encrypted files but there is no guarantee.Some so far encountered obstacles that may prevent decryption are:
- It works only on files encrypted by the original version of CryptoLocker infections; it may or may not work on files encrypted by later versions of ERW.
- Nobody knows if the servers accessed by FireEye and Fox-IT contained all private keys CryptoLocker had used.
- The original CryptoLocker was effectively eliminated late in May, 2014; any later infections will most likely have used different sets of private keys.
My personal conclusion
It is primarily user behavior that protects the computer by always keeping Windows and all other regularly used programs up to date. If all this is accompanied by attention to detail and applied common sense then the computer will most likely remain “healthy” and safe.
In the worst case scenario, that is after your computer got hit by CrypyoLocker or a look-alike having a recent clean backup will be the best medicine against sleepless nights.
As usual I welcome suggestions and comments right here in the blog.
Click here for a categorized Table Of Contents.
Friday, August 8, 2014
2014 Update On Malicious Programs
As far as malicious software is concerned much has changed since I last wrote about it. So here is an updated report on the current situation (summer 2014) ans my personal advice on how to stay safe on the Internet. I will talk about
- Definitions
- How to avoid these troubles and a
- Conclusion
Protective tools for the home user
Definitions:
Malware: Short for malicious software. It is a general term used to describe all viruses, worms, spyware, and pretty much anything that is specifically designed to cause harm to your PC, steal your information or throw never ending torrents of advertisements at you.
Virus: A program that copies itself and infects a PC, spreading from one file to another, and then from one PC to another when infected files are copied or shared.
Spyware: Any software that collects your information without your knowledge and usually sends that information back to the creator(s) so they can use that personal information in some nefarious way.
Scareware: A relatively new type of attack, where a user is tricked into downloading what appears to be an antivirus application, which then proceeds to tell you that your PC is infected with hundreds of viruses, and can only be cleaned if you pay for a full license. Of course, these scareware applications are nothing more than malware that holds your PC hostage until you pay for the “full” version. In many cases you can't uninstall them and/or the render the PC unusable.
Trojan horses: Applications that look like they are doing something innocuous, but secretly have malicious code that does something else. In many cases, trojans will create a backdoor that allows your PC to be remotely controlled, either directly or as part of a botnet—a network of computers also infected with this trojan and/or other malicious software. The major difference between a virus and a Trojan is that trojans don't replicate themselves—they must be installed by an unwitting user.
A computer worm uses a network to send copies of itself to other PCs, usually utilizing a security hole to travel from one computer to the next, often automatically without user intervention and often via email.
Ransomware usually encrypts your files that then are useless to you and some even “lock” your computer. The software requests an often quite substantial payment for the means to restore your files into usable form – which even after payment sometimes fails.
Protective tools for the home user
You will always want to run a specialized anti virus program and a specialized on-demand only malware removal tool. I will recommend the only two programs I have learned to trust over the years – and that are easy enough to handle for the home user.
Anti virus: The release of Microsoft Security Essentials has changed the landscape of antivirus software. We finally have a completely free application that protects against viruses, spyware, and other malware without killing system performance like some of the "suites" tend to do. In my extensive personal experience it barely slows down even relatively slow machines and it's user interface is the easiest to use of all I know.
Don't only take my word for it. AV-Test.org found that it detects 98% of their enormous malware database and AV-Comparatives (a widely known anti-malware testing group) found that MSE was one of only three products that did well at both finding and removing malware.
Anti malware: Modern malware, mostly called PuP (potentially unwanted program), is very different from classic viruses. Most anti-virus programs can not detect PuPs and thus do nothing about it. And, as if to add insult to injury, most of them come on the computer because the user got tricked into allowing their installation.
I recommend Malwarebytes Anti-Malware (MBAM for short). Please download it from these two links only (they both go to the same destination).
MBAM is a time proven product and available in a totally sufficient free version. You have to watch during the original install and when you install a program update. The last window of the installer looks like this:
MBAM is a time proven product and available in a totally sufficient free version. You have to watch during the original install and when you install a program update. The last window of the installer looks like this:
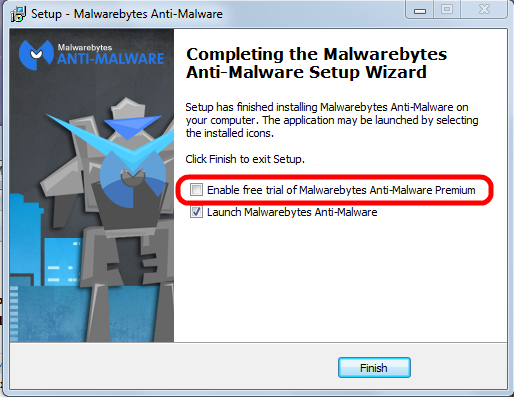
Please pay attention to the marked entry; it's check box is preselected! That means the “trial version” will be activated and after the trial period ends you would have to pay for using the program.
You have to uncheck this check mark.
Eventually the program itself needs to be updated; the installer will run again and again you have to pay attention to this little detail to avoid the for-pay version!
See this article on how to correctly use MBAM.
See this article on how to correctly use MBAM.
How to avoid all these troubles
When it comes to protecting yourself, it's laughable how many people install multiple antivirus applications but don't keep their system updated with the latest patches for the operating system.
If everybody would simply keep their system and all programs up to date, we wouldn't have to worry so much about these problems. If the constant rebooting action of Windows Update has you frustrated, you can always temporarily delay the reboot; remember, only after the reboot the patches are completely installed and active to protect your computer..
Keeping your applications updated is critically important to protect your computer's security. Your firewall won't protect you, and an antivirus software is unlikely to help if you're using an old, vulnerable version of Adobe Flash or Adobe Reader.
Conclusion
In the end, good browsing habits and common sense should be your first line of defense against any kind of malware. I recommend to always run a good security suite like MSE and additionally to use MBAM as an on-demand scanner. That way you're as well protected as easily possible and you can scan your system for malware whenever you want.
So here's the bottom line: In my not so insignificant experience MSE and the on-demand free version MBAM work very well together . Coupled with good browsing habits and common sense this a good combination of security tools and judiciously using them should keep you well protected.
As usual I welcome comments and suggestions right here in the blog. Thank you in advance.
Click here for a categorized Table Of Contents.
Click here for a categorized Table Of Contents.
Thursday, February 20, 2014
Voicemail via Email? No Way!
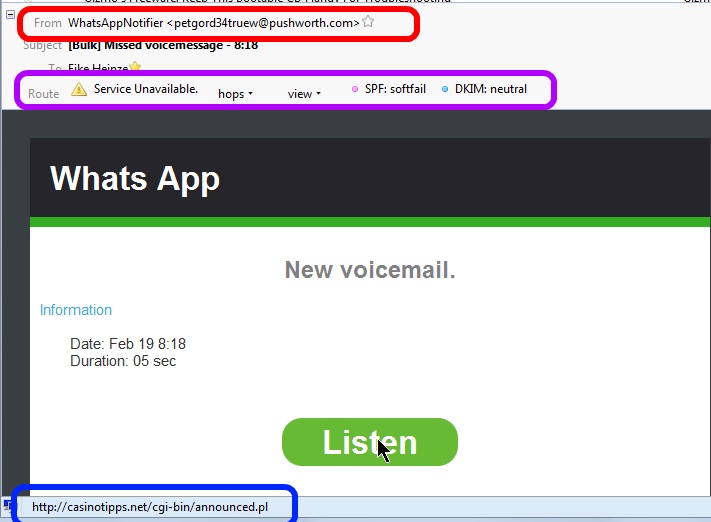
Here is yet another example of a scam I hear often about. This is a screen shot of what I saw in my email program:
At first glance a friendly, nicely formatted and really "professional" looking email.
Three things caught my attention before I would have clicked on "Listen";
- Red highlight: The sender address seems to come from "@pushworth.com". Big discrepancy to the supposes (company?) name "Whats App".
In my mind the warning lights went on.
- Purple highlight: The sender disguised very well the actual route the email had taken. That shows technical know how and (criminal?) intent.
By now the warning bells where ringing loud.
- Blue highlight: When I rested the mouse cursor on the pretty "Listen" button the link behind this button translated to "casinotipps.net". Casino tips and forwarding voice mails via email? Oh Please, don't think I am that dumb.
Now I was already chuckling; just another scam email.
But I know from experience that there are simple souls out there who did click on "Listen"; although the mail they had gotten likely looked different.
Actually I should be thanking the creator of this scam because he keeps me in the business of cleaning up virus infected computers.
As usual I welcome suggestions and comments right here in the blog.
Click here for a categorized Table Of Contents.
Tuesday, February 18, 2014
New Twist - Old Scam
Whether you ever would read The New York Times or whatever your political stance is,
if you have a computer you NEED to read this NYT article.
The age old story of "User Beware" with a macabre twist.
As usual I welcome suggestions and comments right here in the blog.
Click here for a categorized Table Of Contents.
.
Tuesday, January 28, 2014
Driver's License for Computers?
If you drive down the highway, you’re at risk of getting in a car wreck.
If you log onto the Internet, you’re at risk of identity theft, viruses and malware — no matter who you are or where you’re coming from.
Like safe driving, maintaining a secure computer is all about being attentive, defensive, proactive and educated.
This is why drivers of cars need to be trained and licensed to drive.
This is why many computer professionals think computer users should be educated and licensed to browse the Internet and handle email.
What about your "Internet License"?
As usual I welcome suggestions and comments right here in the blog.
Click here for a categorized Table Of Contents.
Click here for a categorized Table Of Contents.
Thursday, December 5, 2013
Virus Check BEFORE Download
I assume that you know about Virustotal (VT). If you still don't now than I am at a loss of words- which rarely if ever happens to me. But enough of my puny attempts on being funny.
With VT you can check any reasonably sized file (up to 64MB) that already is stored on your computer for viruses. What if you want to check a file for viruses before you actually download it?
If you use a web browser other than Internet Explorer you could install an extension.
- In Mozilla Firefox you can install the VTzilla extension.
- In Google Chrome you can install the VTchromizer extension.
- In Opera you can install the VTopera extension.
VT will upload and test the file in it's usual manner and presto you have a good idea whether the file in question is "clean".
If you feel challenged by the idea to install an extension in Firefox don't despair, I can do that remotely.
As usual I welcome suggestions and comments right here in the blog.
Click here for a categorized Table Of Contents.
Click here for a categorized Table Of Contents.
Labels:
antivirus,
Firefox,
Google Chrome,
HowTo,
Internet Explorer,
malware,
Opera,
Rogue,
security,
software,
support,
virus,
Virustotal
Monday, October 28, 2013
How Malware Gets Installed
You hear from me that your computer got infected with malware, especially PuPs, and you ask:
"How did that stuff get on my computer? I did not download or install it".Sorry, but in most cases you did give permission to install that garbage alongside some legitimate install or update. You did not do it consciously, you got duped or tricked into allowing the installation. See this article for just one all too common example.
These tricks can have many different shapes and forms. They all are designed to trick or fool us into allowing the garbage to get installed alongside a legitimate program or update. User beware!
One of the more and more common forms is a legitimate install or update that asks something along the lines of
- Default (or Express) install (recommended)
- Custom install (for experienced users)
Simple answer: Money! The authors of PuPs pay for their stuff being bundled with legitimate software. There is a lot of money to be made from advertising!
Distributing viruses is illegal, distributing "search helpers" or tool bars is not!
My advice: When you have to choose between Default and Custom installs always(!) click Custom; it is the only way to check for PuPs because so far at least they are being offered with some sort of a choice to decline or skip them.
If you are in doubt take a screen shot of the window(s) that sparked your suspicion, postpone the install and ask me in an email about it; don't forget to attach the screen shot please.
As usual I welcome suggestions and comments right here in the blog.
Click here for a categorized Table Of Contents.
Wednesday, September 18, 2013
PUPs - No Virus But Just As Nasty
Updated Oct. 27th, 2013
The latest and fast growing trend of cyber crime against the unsuspecting user of a Windows PC is a new breed of malware, so called PuP programs (Potentially Unwanted Program).
These programs technically are not viruses; that is why anti virus programs don't find them - although there are some special programs for geeks and technicians that can clean this stuff from your computer.
You can easily check your computer for at least a few the most commonly encountered names.
- Open the Control Panel
- Set "View by" in the right top corner to Small Icons and
- Open Programs and Features
The somewhat good news: Many of these pieces of trouble can be uninstalled, that is removed, from right there in the Programs and Features window where you just found them.
The really BAD news: Even if you uninstall them successfully there will be leftovers in web browsers and other important locations in the operating system.; especially Google Chrome seems to be likely to retain some of that. These leftover entries can be numerous, affect functioning of web browser(s) and significantly hamper the computer; they can only be removed with some specially written very detail oriented clean-up programs.
Well, you know who can help, don't you?
Please remember: Toolbars are forbidden, no matter who promises what, no matter how tempting the name and no matter who made the tool bar! If you find any toolbars remove them right away.
If you find folders with names from random letters or numbers like for example:
pgmfkblbflahhponhjmkcnpjinenhlnc
you have a clear indicator of malicious software. You know who can help, don't you?
If you wonder how all this stuff got on the computer then please read the explanation here.
As usual I welcome suggestions and comments right here in the blog.
Click here for a categorized Table Of Contents.
Tuesday, September 17, 2013
Cybercrime
If you ever wondered about the how and why of virus programs, cyber crime and all that nasty stuff then please take 18 minutes out of your busy schedule and watch this video.
As usual I welcome suggestions and comments right here in the blog.
Click here for a categorized Table Of Contents.
Labels:
antivirus,
crapware,
deception,
foistware,
Gunk,
Hijack,
Key Logger,
non-computer,
online,
recommended,
scam,
security,
Social Media,
social networks,
support,
Trojan,
virus,
warning
Thursday, February 28, 2013
Phone Scams - Way Too Many!
It has happened again: One of my customers got caught by a phone scam. This lady (elderly, pardon me) got a phone call claiming to be from a Microsoft partner company and informing her that her computer had reported a virus infection and needed to be thoroughly cleaned.
The lady fell for the ruse and gave the caller her debit/credit card information and allowed the guy remote access to her computer.
She ended up with almost $200 less in her bank account and a nasty virus program on her computer. Just the removal of this virus cost her additionally two hours of my time.
Currently I hear similar stories way too often.
Please read this article in Microsoft's Safety & Security center; it gives you everything you need to know. With this knowledge and a dash of common sense you can easily detect these scams.
Stay safe.
As usual I welcome comments and suggestions right here in the blog. Thank you in advance.
Click here for a categorized Table Of Contents.
Monday, August 13, 2012
FBI Warning "freezing" Your Computer?
Caution, the latest scam out there purports to be from the FBI. It is not!
In this warning the FBI states that:
There is a new “drive-by” virus on the Internet, and it often carries a fake message—and fine—purportedly from the FBI.
“We’re getting inundated with complaints,” said Donna Gregory of the Internet Crime Complaint Center (IC3), referring to the virus known as Reveton ransomware, which is designed to extort money from its victims.
Reveton is described as drive-by malware because unlike many viruses—which activate when users open a file or attachment—this one can install itself when users simply click on a compromised website. Once infected, the victim’s computer immediately locks, and the monitor displays a screen stating there has been a violation of federal law.
The bogus message goes on to say that the user’s Internet address was identified by the FBI or the Department of Justice’s Computer Crime and Intellectual Property Section as having been associated with child pornography sites or other illegal online activity. To unlock their machines, users are required to pay a fine using a prepaid money card service.Mostly the fake message states that your computer was used for "illegal use of downloaded media, under-age porn viewing, or computer-use negligence". Naturally none of that is true.
It is a fairly primitive scam but quite a few people seem to be driven by their bad conscience to pay. They are out of some money and they have handed their credit card info directly to the crooks!
No US government agency would ask a perpetrator online to directly pay a fine. In the US you would get indicted in a court of law. "Direct payment" happens only in high corruption countries and/or under dictatorships; it's called a bribe.
The nasty thing with this virus is that the home user generally does not have the technical expertise to remove this nasty piece of software; you will have to call a competent technician.
My customers know who to call; do you?
As usual I welcome comments and suggestions right here in the blog. Thank you in advance.
Click here for a categorized Table Of Contents.
Tuesday, June 12, 2012
Why I Shun Some Microsoft Programs
This is something
that I need to explain to almost every
new customer; so it makes sense to write it down – finally.
For technical purists: I know my
wording is not always technically 100% correct but this blog is written for totally
non-technical people; their understanding of the concepts is more important to
me than expressing my thoughts technically fully correct. I ask your
forgiveness.
In the 1990s
Microsoft developed a programming technology known as ActiveX. This technology naturally
is widely used in all major Microsoft products. ActiveX programs require the so called “ActiveX
environment” on any given computer to be able to work. Consequently all major
Microsoft programs contain and supply an ActiveX environment.
In December
2009 Microsoft operating systems powered more than 92% of installed computers
according to this ArsTechnica
article. This market share has somewhat shrunk but I believe I still can
say: Since ActiveX was introduced Microsoft has become a world encompassing
monopoly.
According to
Internet World Stats currently
there are over 2.3 billion Internet users worldwide. Around
80% to 90% of these people use a computer that is run by an operating system
from Microsoft.
What is a
crook going to do if he wants to (ab-) use your computer for his purpose? What
programming technology or programming language is he going to choose? Likely he
will choose the programming language that will give him access to the largest
number of computers, machines run by a Microsoft operating systems.
Around 2006
there were estimates that about 75% to 80% of all viruses were written in
ActiveX. I have not found current statistics but that percentage is lower now. By
my personal estimate currently ca. 50% to 60% of viruses are still written in
ActiveX.
My
conclusion: Just by not using certain
Microsoft programs we can easily avoid common ActiveX viruses! Microsoft programs
that I avoid are primarily:
- Internet Explorer
- Any and all Microsoft email programs
- Windows Media Player
- MS Word, Excel and PowerPoint when I need to tap into Internet connected features
- Microsoft Messenger (a chat program)
How do I “get
to the Internet” and write letters and so on you ask? The alternatives of my choice are all free, free as in no money at all and safe as far as malicious ActiveX programs go:
- Mozilla Firefox (web browser)
- Mozilla Thunderbird (email client)
- VideoLan VLC (media player)
- Libre Office (office suite)
- Pidgin (a chat program)
As usual I
welcome comments and suggestions right here in the blog. Thank you in advance.
Click here
for a categorized Table Of Contents.
Labels:
ActiveX,
general,
LibreOffice,
recommended,
security,
virus
Wednesday, May 30, 2012
Hacked Passwords
Currently it happens way too often that passwords of email accounts get hacked. The compromised accounts get used to send out spam emails that will one way or another make money for the crooks behind this scam. Mainly affected are accounts that end with
- @yahoo.com
- @hotmail.com
- @aol.com
- @att.net
- @sbcglobal.net
Affected accounts are used to send out spam email that look mostly like that:
this is rather awesome http://www.eudonews.net/biz/?read=6036326
The leading text and readable part of the link can be different but so far the general format has been similar. I expect that sooner or later (I am afraid sooner) the crooks will replace the leading text with more intriguing and/or salacious creations.
Again and again I have to say: Even when such an email seems to come from someone you know DO NOT CLICK on the link! The sender address in an email is NOT trustworthy, it can easily be faked to show whatever the crook wants you to see!
The links always lead to known malicious and untrustworthy websites. One way or another the crooks make money, lots of money. Some gang that recently got
busted had collected about 14Million dollars.
The accounts could get hacked because the passwords were too short, simple, easy or any combination thereof.
The accounts could get hacked because the passwords were too short, simple, easy or any combination thereof.
In April 2011 I wrote an article about "Passwords too simple - What to do about it". It still is valid!
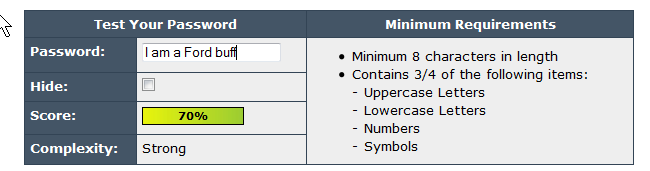
Just as an example: A collector of classic cars uses the password "fordbuff". Eight character length is by some technicians considered to be a fairly good password. BUT see this from passwordmeter.com:
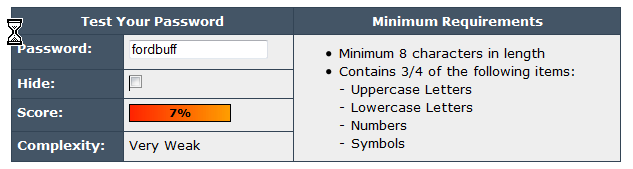
Had he chosen "I am a Ford buff" it looks like this:
And now look at the result for "Driving 2 Fords":

Impressive differences, aren't they? And where come these differences from? Example two contains capital letters and special characters (spaces), example three contains an additional number.
If you have not yet done so please read my April 2011 article about "Passwords too simple - What to do about it". It still is valid!
And another possible reason for your account passwords being hacked may
be that you have a password sniffing virus on your machine.
Do you already run Microsoft Security Essentials or are you still
on Avast, AVG or Avira, "the other" free anti-virus programs?
Conclusion: A simple little sentence with a number somewhere in it
is way better than any single word!
Click here for a categorized Table Of Contents.
Tuesday, May 15, 2012
DNS Changer - as promised on the last radio show
Well, I have gotten a few calls because of the ridiculously exaggerated comments and reporting in the press.
If you want the low down and the details please grab a cup of Joe or a beer or whatever else you like, settle in your favorite chair and head over to this article on the Windows Secrets newsletter dated May 2nd. 2012.
You'll have to read oll the way to the end to find the link to the web site that is testing your computer for an eventual DNS Changer infection. SHOULD against all expectations your computer be infected and if you can't get rid of the virus yourself then I would be more than willing to help.
As usual I welcome comments and suggestions right here in the blog. Thank you in advance.
Click here for a categorized Table Of Contents.
If you want the low down and the details please grab a cup of Joe or a beer or whatever else you like, settle in your favorite chair and head over to this article on the Windows Secrets newsletter dated May 2nd. 2012.
You'll have to read oll the way to the end to find the link to the web site that is testing your computer for an eventual DNS Changer infection. SHOULD against all expectations your computer be infected and if you can't get rid of the virus yourself then I would be more than willing to help.
As usual I welcome comments and suggestions right here in the blog. Thank you in advance.
Click here for a categorized Table Of Contents.
Labels:
antivirus,
DNS Changer,
malware,
security,
virus
Wednesday, January 25, 2012
Computer 101 - The 2012 Edition
Disclosure:
Recently I found this article on a blog called The Consumerist. I liked the contents of this article very much but it clearly was written by a computer nerd for other computer nerds.
I took the liberty to re-write most of the article in a form and language that I hope is better suited for my customers. Here it is:
- Keep all your data backed up.
Put your data on an external disk drive, upload it to a safe storage website, copy it to another computer or even on a CD or a DVD (most cumbersome!), somewhere, anywhere but please back up your data files!
I am perfectly aware that many of my customers will have issues in setting everything up correctly but as usual I can help.
Having your data on your computer only is NO GOOD, having data files in two places is a MUST. If one of these sets of data files fails you need to create another second storage location! This will save you $$ and a lot of aggravation.
Manufacturer warranties do not cover your data files; you need to protect them yourself. Back up your documents, pictures, emails, email addresses (or contacts), bookmarks (or favorites), tax files, music, videos and ANY business information you may have.
The only exception to my rule "free software for everything" covers data backup. You need a sufficiently large external disk drive and a piece of software costing $30 per computer.
If set up correctly this program will keep all your data files automatically up to date on the external disk drive without you having to do anything except the initial set up. As usual I can help with that.
- Have a current recovery disc for each computer you have.
This is your licensed copy of your OS. You no longer get operating system disks with a new computer; it’s all stored on the disk drive. It is specific to your computer's internals like processor, mother board, sound and graphics. It has the device drivers your computer needs to do its most basic tasks. Burn a recovery disk on to DVDs right away when you get your computer and put the DVD somewhere safe. It may easily take up to 3 hours to do.
If you lose the recovery disk then you can order a new one from your manufacturer for between 15 and 50 dollars, depending on the brand. HP is usually cheaper, Sony is wickedly expensive. They take about 2 or 3 weeks to arrive; that is a looong wait if you need them NOW to replace a hard drive or to fix Windows.
There is a significant difference between recovery disks and a repair disk that you need to be aware of. You can read about that here. You have to be aware of that significant difference. And you have to be aware of the fact that if you have to use these recovery disks your computer will be thrown back to exactly the state it was in at the very moment when the recovery disks where created! Here I am talking about recovery disks created with the standard Windows Vista and Windows 7 system tools, not disks created with manufacturer specific programs; the latter reset your computer to original factory new state. You don't want to go back there losing all updates and so on.
If for whatever reason you can neither buy recovery disks from the manufacturer nor create your own disks then, as a last resort, you can purchase a full copy of Windows 7 for about $100.
- One antivirus at a time, please.
Two antivirus programs running concurrently is like pushing two fat pigs together through a dog door, neither can get through the door correctly and they block each other from functioning properly.
Two antivirus or security programs can tear nasty holes in your operating system depending on which ones you are trying to combine (I have seen it!) or at least they will SLOW DOWN YOUR COMPUTER TO A CRAWL because two systems are trying to scan your every move as well as each others moves.
More than one antivirus or security program running concurrently is usually LESS protection than one good one.
Your new computer most likely came with a trial of some sort of “security” software pre-installed. All these pre-installed antivirus or security programs will cost money, every year! Remove this stuff because you don’t need to pay for a good antivirus program!
Remove the “old” antivirus program before installing a new one; even if they are expired they will get in each other‘s way! And some of them don’t even uninstall correctly. I have uninstalled Norton, McAfee and other security programs and upon detailed inspection found some left over parts of these systems still sitting in and actually running on the computer. This inspection is not trivial at all; it takes very special programs and a lot of detailed know how to do it correctly.
Install the free program Microsoft Security Essentials; you can read here how to do that correctly.
- Do not install any tool bars.
Did you hear me? Please DO NOT INSTALL ANY TOOL BARS!
ALL toolbars are bloatware, they will slow down your internet connection and eventually even crash your web browser.
You don't need any of them, no matter how well known the company is that wants to force the tool bar on your computer!
Tool bars take up screen space and they will end up affecting performance and sometimes even security.
Please DO NOT INSTALL ANY TOOL BARS!
- "Free" stuff can be expensive:
Web sites that offer free games, movies, music (torrent sites!), pornography and even free social networking sites are riddled with viruses. Virus removal can be time and thus $$ consuming.
Viruses are a software issue and are considered private data, they are not covered by any manufacturer warranty.
Be safe and smart on the internet, use common sense and be vigilant.
Keep your important software up to date; read more details about updating here.
- Despite everything said in paragraph #5 above: Excellent free software is available for almost any functionality you can imagine and I can point you in the correct direction, I can show you where to find it.
- Computers don’t like liquids.
This includes water, coke, beer, soup, bodily fluids and excessive and/or aggressive cleaners.
Don't spray screen cleaners directly on your screen, spray it on your lint free cleaning cloth and then wipe the screen. Even a mist of any liquid can cause damage.
Computers also don’t like gravity or being punched. Throwing or punching a computer will probably cause a lot more damage and not fix any issue, be it speed or erratic behavior.
- No computer is immortal.
Computer technology changes at an extremely fast rate. Average computer life spans are mere 2-3 years for laptops or closer to 4-5 years for desktop computers. This makes sense, because laptops undergo more stress from movement, impact and temperature changes. Many laptops are prone to overheating if you have them sitting “just” on your lap, on a table cloth(!) or on a pillow. NEVER EVER do that, always have your notebook computer on a solid, even surface like wooden tabletop, a counter top or a board.
Your computer uses electricity that circulates through lots of electronic components that in turn can get really hot. Many portable computers eventually burn out. And if you have your data backed up, you'll be up and running on a new computer in no time.
Click here for a categorized Table Of Contents.
Subscribe to:
Posts (Atom)