Showing posts with label security. Show all posts
Showing posts with label security. Show all posts
Monday, April 6, 2020
Amazon Prime member? WARNING!
I have an Amazon account AND an Amazon Prime membership.
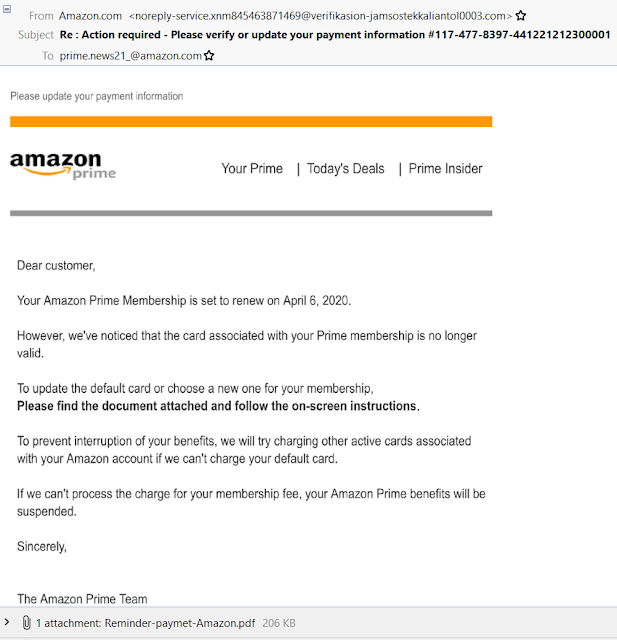
I received an email and I want to show it in a screen shot:
On first glance nothing really alarming, right?
BUT:
The sender email address (labeled From:) looks to me totally wacky and the Reply-To address (labeled To:) IMHO is equally unlikely.
The warning bells in my mind started to ring loud and clear.
My wife and I use the same Amazon account all the time and thus I know that the payment method is correct and that it works.
Even saving the attached PDF document to my computer and then scanning it with Malwarebytes did not show any alarms or warnings.
So I opened the file in my PDF reader to check it out in more detail.
The PDF document contains a link and a BIG button to supposedly go to Amazon's account and payment method web page.
BUT this is what the link and the button actually would have sent my web browser to:
https://t.umblr.com/redirect?z=https%3A%2F%2Fam1zn-updtaeinfmtaonsupdtee-verifyconfimationss76757855.com%2F%3Fsigninn-&t=NmVmZTU1YjdlNTBkODkzYjc0NTg1NzM0MTI2YWNhNWJkOGNiZGRjZSxjYTVkNGQyNzY5ZjI4OGQ2OGFiZjQ2ZDJmOTg3NjZlMTZkNTI5M2Y3
What a crazy nightmare - and for me a clear indicator that something was VERY WRONG!
I went to Amazon.com and checked in my account settings and voila, my Prime membership is paid for until September and the payment information is correct.
Naturally I will report this to Amazon.
MY conclusion as far it concerns you?
Be super vigilant, never trust an email and do NOT be complacent!
Yes, IMHO it is complacent to "just click" on the big button or the link in the PDF file rather than verifying the claim made in the PDF file independent of the email and it's attachment!
Stay safe, stay vigilant and pay attention to the details!
Thursday, March 5, 2020
About Trackers
General information about Trackers and Tracking Cookies:
The Guardian has some interesting reading about trackers and tracking cookies.
Yes, the Guardian article is from 2012 and these technologies have evolved and become more sinister and secretive.
HowToGeek.com is a very reliable web site with all sorts of good how-to advice. Their article from 2016 The Many Ways Websites Track You Online is worth your time.
But if you want a shortcut without the background knowledge then go and install in your Firefox web browser the extension named DuckDuckGo Privacy Essentials.
Here are four more articles from well reputed sources about this extension:
Stay safe!
Sunday, November 4, 2018
The UGLY underbelly of the End User License Agreement
All of us - well, almost all of us have been conditioned to accept the so called "End User License Agreement" (EULA) for next to everything. Sometimes we agree unknowingly just by turning a new gadget ON; my classical example for that is Windows 10 with it's 12,000 words long EULA.
EVERY app on our phones,
EVERY program ever installed on our computers,
EVERY so called "smart" or "connected" TV in our living rooms,
EVERY supposedly "intelligent" device that recognizes "Google Hello" or is "Alexa enabled",
EVERY of the many useful things that require an Internet connection and an app on a smart phone
and many more things too numerous to list here can be used to spy on us.
Hard to believe? Please listen to this 12 minutes long TED talk, maybe it will change your view.
Stay safe!
Friday, September 14, 2018
Why I Don't Like Windows 10 and MS
In quite a few articles on this blog I have referred to, quoted from or linked to one of the web sites I regularly draw information from; I am talking about Tech Support Alert aka Gizmo's Freeware.
Two days ago they published an article titled "Windows 10 connects to these websites after a clean installation". Since many of my customers are not very technically minded let me quote some points that I consider to be the important details.
IMHO it is, to say the least, misleading to use Microsoft's wording "telemetry" when our Windows 10 systems talk to Microsoft [MS] all the time without ever having asked our permission. They even don't ever tell us about the simple fact that they do that; you have to be a technology geek and read lots of very technical stuff to even become aware of what is going on.
The article lists 20 web sites that Windows 10 connect to when you start a brand new Windows 10 system. All these sites collect technical information about our computers and about us. As a simple example: Why does MS want or need to know where I am? That is information I personally would only disclose to the police if they ever wanted or needed to know that.
Here is list from above mentioned article. I have added the bold typeface in Line 1.
Windows 10 connects to one or more websites in these categories:All this can on slower Internet connections add significantly to the time it takes for the system to start up. I have experienced that quite often when a sluggish or outright slow system all of a sudden works with normal reaction times after all that got turned off.
- Cortana and Search
- Certificates
- Device authentication
- Device metadata
- Diagnostic data
- Font streaming
- Licensing
- Location
- Maps
- Microsoft account
- Microsoft store
- Network connection status indicator (NCSI)
- Office
- OneDrive
- Settings
- Skype
- Windows Defender
- Windows Spotlight
- Windows Update
- Microsoft forward link redirection service (FWLink)
And to top it off, the program I use to turn off this talking back to MS is from a well reputed company and totally free.
Any questions or comments? Pleas use the Comment feature of this blog.
Please stay safe.
Labels:
Gunk,
Microsoft,
new computer,
rant,
security,
speed,
warning,
Windows 10
Sunday, August 12, 2018
Old Scam - New Clothes
A scammer from India came up with a new twist of an old ruse.
Look at this screen shot of the offending email as shown in my email program:
Btw. following references to the blue or red squares do in no way refer to BattleBots. 😉
In the blue square we have the sender's email address. I believe that NO administrator in the whole wide world would ever use an AOL email account for his official business. Some criticism of AOL can be found here.
In the first red square you see my cursor on the VERIFY NOW link and because of that you can see in the second red square the textual representation of what web page that link would actually send my browser to - if I were sufficiently un-attentive to click my mouse in that situation.
The target web page is on a server in India at "managershub"! You don't see that? Learn how to read URLs.
And I don't even use what the scammer refers to as a "Web-mail system".
To top it off there are three simple spelling errors or typos in the short text of the email; unprofessional to the hilt!
Sum total: An old but time honored scam in a new dress - but not even a fancy dress.
Again it comes down to the first of my ten commandments for safe computing:
Thou shalt read and think(!) before you click.Stay safe!
Saturday, July 7, 2018
URGENT ALERT! For users of any Apple thinghy!
Hi y'all and thanks for reading this.
If you or someone in your household has any piece of equipment from Apple, like an iPhone, iPad, iPod or the like then
this is for you!
Since iPhones a.s.o. are so common nowadays the crooks are targeting you. Look at the email I just got in a partial screen shot of the Thunderbird screen:
I have marked the give-away items with colored rectangles as follows:
Blue: I don't have an Apple account! Ha, ha, ha.
Purple: The email does not even come from Apple!
Green: My cursor pointing to the "Verify..." button.
Red: The URL (web site address) that the "Verify..." button actually is pointing to; it has NOTHING AT ALL to do with Apple.
To be addressed as "Dear ejheinze@att.net" is so unprofessional this alone would be reason enough to click on the Delete button!
The item in the red rectangle I see only because I told my email program to show this and because the cursor is on the "Verify..." button. I believe none of this needs further clarification. Should you have any questions please feel free to ask me, preferably in an email.
A general remark:
If the program you use to read your emails
does not show you any of the information in blue, purple and red
then you potentially endanger your computer!
does not show you any of the information in blue, purple and red
then you potentially endanger your computer!
Any Questions? Please feel free to ask me, preferably in an email.
Stay safe.
Wednesday, July 26, 2017
How to Protect Yourself and Your Computer on the Internet
Sometimes I am still amazed by the degree of how clueless some people are as far as the most basic ways are concerned to stay safe on the Internet.
I don't want to repeat myself here and I don't want to sound like a broken record either. Oops, many younger readers would not even know what that means...
Anyway, here is a good and easy to read but admittedly fairly long article titled
Basic Computer Security: How to Protect Yourself from Viruses, Hackers, and Thieves
My regular readers will recognize that I quite often link to articles on How-To Geek. At least the articles about computers are an easy read and correct on top of it.
Stay safe.
Saturday, July 22, 2017
Why NOT TO USE Internet Explorer
About one to two times every month I encounter customers who react clearly with doubt or outright disbelief when I tell them NOT TO USE Internet Explorer. IE is Microsoft's web browser with roots in the mid 1990s. That is in computer terms ancient!
Finally I found an article on maketecheasier.com that explains the "why" in easily understandable terms. You find it here. Enjoy the read and please, please pass the word to your relatives and friends.
And if you are only a little bit like me you want to turn off IE totally. You find instructions on how to do that here.
Stay safe.
Friday, July 21, 2017
The Skinny ...
... about the latest outbreak of Encrypting Ransomware.
The original of this text was written by Ken Dwight, aka The Virus Doctor. I am an alumnus of his Virus Remediation Training and make this text available for my customers with his kind permission. Thanks Ken.
All my customers are advised to weekly initiate a check for Windows Updates. If they followed that advice their computers were protected and they don't need to care about these two overly "hyped up" virus outbreaks.
Stay safe.
The original of this text was written by Ken Dwight, aka The Virus Doctor. I am an alumnus of his Virus Remediation Training and make this text available for my customers with his kind permission. Thanks Ken.
As with malware in general, encrypting ransomware is continually changing. Most of these changes are evolutionary and somewhat predictable. As such, they don’t call for any significant changes in the methodology to be used in dealing with them.That was it.
Some recent developments in specific families and strains of encrypting ransomware are
significant enough to justify an update to the IT Support technician’s strategies and tactics for handling them effectively.
There are primarily two families of such ransomware that warrant this attention. Multiple names have been assigned to these families, but this discussion will use the names that are most frequently found in credible press coverage of these outbreaks.
WannaCry was released into the wild on May 12, 2017. According to most reports, it infected at least 200,000 computers, in more than 150 countries. This ransomware spawned its own Wikipedia entry, at
https://en.wikipedia.org/wiki/WannaCry_ransomware_attack.
The more recent attack, erroneously known as Petya, but more accurately referred to as
NotPetya, first struck on June 27, 2017. There are no estimates of the total number of computers infected by this malware, or the number of countries represented. But it clearly targeted businesses and organizations in Ukraine, with some 80% of the infections found there. This ransomware also has its own Wikipedia entry, at
https://en.wikipedia.org/wiki/2017_cyberattacks_on_Ukraine.
These two families of ransomware have several characteristics in common. Probably the most notable is the widespread coverage both received in the general press. While malware generally goes unreported in the non-trade press, these attacks were the exception to that rule. Fueling the press coverage was the revelation that both of these attacks were based on exploits developed by, and subsequently stolen from, the U. S. National Security Agency (NSA).
Interestingly enough, I have not seen any of these infections first-hand, nor have I received reports from any graduates of my Virus Remediation Training workshops that they have encountered computers encrypted by either of these families of ransomware. Considering the fact that hundreds of IT Support Techs fall into this category, in most of the United States + 7 foreign countries, I can only speculate that the actual infection rate is much less widespread than the press coverage would lead one to believe.
Another common denominator between these two infections was the fact that the vulnerability in Windows that was used for both of these attacks had been patched by Microsoft in their March, 2017 Windows Updates; any computer with that update applied would not have been infected by either of these pieces of malware.
Two NSA exploits were used in both of these attack scenarios; they are named EternalBlue and DoublePulsar. A free EternalBlue vulnerability scanner is available for download from http://omerez.com/eternal-blues-worldwide-statistics/. As of mid-July, 2017 more than 10 million IPs have been scanned; the majority of hosts scanned (53.82%) still have SMBv1 enabled, and 1 out of 9 hosts in a network is vulnerable to EternalBlue.
The WannaCry malware included a “Kill switch” which was discovered by a malware researcher and activated to disable the infection from spreading any further. No such kill switch has been found for NotPetya, but a “Vaccine” has been developed to protect against it. More details from Bleeping Computer at https://www.bleepingcomputer.com/news/security/vaccine-not-killswitch-found-for-petya-notpetya-ransomware-outbreak/.
Another important difference between these two families of malware involves the type of
encryption they perform on the victim’s hard drive. WannaCry, like most encrypting
ransomware, encrypts each individual file. It also changes the filename to end with an extension of .wcry.
On the other hand, NotPetya encrypts the entire hard drive and replaces the Master Boot Record with its own version. While the encryption is taking place, the malware displays a screen that looks like a chkdsk operation is being performed; when the whole-disk encryption is complete, it forces a reboot.
Upon the reboot, the modified MBR causes the ransom note to be displayed, with instructions to pay $300 USD in Bitcoin; after 72 hours, the ransom increases to $600 USD. Because of the modified MBR, at this point it is not possible to boot into a normal Windows environment.
As of this writing there is no means to pay the ransom; even if the ransom is paid, there appears to be no way to decrypt the hard drive or restore it to normal operation. Consequently, there is no reason to even consider paying the ransom.
Back to WannaCry, there have been some reports of successful decryption after paying the ransom. But here again, I have no first-hand (or even second-hand) reports from victims of this family of ransomware.
Those are the most recent, high-profile developments in the field of encrypting ransomware. But it’s a pretty safe bet they won’t be the last. This category of malware continues to evolve and become more sophisticated and more insidious. It has crossed the threshold of being a billion-dollar industry; that success will attract more and more criminals who are lured by the promise of easy money. Our prospects for future employment remain secure!
All my customers are advised to weekly initiate a check for Windows Updates. If they followed that advice their computers were protected and they don't need to care about these two overly "hyped up" virus outbreaks.
Stay safe.
Wednesday, April 26, 2017
Nothing New?
I got an email from a long time customer who asked me
... where have you been? Not on the Blog in three months...Here is my reply to him:
Thanks for checking the blog.And DO NOT click on links in emails! Check if the link goes to the correct web site! Rest your cursor on the link and look at the left bottom corner of the browser window; there you should see the text of the target URL ( = Internet address) that your browser will take you to if you click on that link. Learn to correctly read these URLs!
There is nothing new -- and that means no bad news and that is good news, right?
It still is the "old" story"; ransomware is at the top of the list of nasty programs.
The only way to avoid that junk fairly reliably - but not guaranteed - is NEVER to click on any attachment to any email!
Save the attachment to your desktop, upload the attachment to VirusTotal.com and have it checked there.
Even only one negative result is enough for me to tell the sender to check his attachments himself and stop sending out potentially infected junk files.
Stay safe!
Monday, January 9, 2017
How to stay safe in 2017 - Short List
Here is a short list of in my experience the most important steps you can take to keep your computer and your data safe. have I have added e few remarks for clarification.
- Update your software.
Not only Windows but all other regularly used programs as well;
for a Windows PC this includes (but is not limited to)
- Adobe Flash (beware of fake download sites!)
- Adobe Shockwave
- Web browser(s)
- Email client
- Java (if installed; mostly Java is not needed at all!)
- Office programs
We always have to keep in mind that some programs still don't update automatically and quietly in the background! Checking manually hardly ever has hurt anything.
- Back-up to an external hard drive.
Done regularly and correctly this currently is the only protection against ransomware viruses!
- Use a password manager.
For single machines see Keepass, for more than one machine see LastPass and include all cell phones and tablets in the count!
- Use a unique password for every account.
Everybody has many, many accounts; you need a password manager!
- Use random passwords
Easily done only with a password manager!
- Turn on two-step verification everywhere you can.
If you have a cell phone that you really use, otherwise this is pretty useless.
- Read and think(!) before you click.
"My" first commandment for safe computing.
- Enable full-disk encryption
On a single home computer? Only protects your data when the machine gets stolen.
- Put a six-digit PIN on your phone and set the phone to wipe it's contents if the PIN is guessed wrongly too many times.
Stay safe.
Labels:
browser,
encryption,
Flash Player,
general,
HowTo,
Java,
LibreOffice,
MS Office,
OpenOffice,
password,
ransomware,
recommended,
security
Tuesday, October 4, 2016
The newest Scam - Beware
The newest telephone scam I heard of is the Microsoft Licensing Scam. You may get a phone call or a voice mail saying something like this (phone numbers deliberately obscured):
“This is to notify you that your Microsoft Windows license key has been expired in your computer so Microsoft Corporation has stopped the services in your computer. To renew the Windows license key, please call 866 XXX XXXX. Let me repeat. This is to notify you that your Microsoft Windows license key has been expired in your computer so Microsoft Corporation has stopped the services in your computer. To renew the Windows license key, please call 866 XXX XXXX. I will repeat 866 XXX XXXX.”The message obviously was from a computer generated, sort of "mechanical" voice and the stilted English suggest a non-native English speaker behind the whole thing.
Any messages about licensing issues truly from Microsoft would pop up on your computer's screen only during installation or activation. And we all know, if only from experience, that a Microsoft license for the Operating System comes with the computer when you buy it and it is good for the lifetime of the machine.
In Windows services are programs running in the background; they are required for even basic functions of the computer. A computer would not work at all without the required services running in the background.
In the case I read about the recipient happened to be a very, very experienced Windows user; the gentleman called back the 866 number from the message; he said about that call:
"Because the number was toll free, I called it just to see what would happen. An answering machine invited me to leave a message and my number for a callback — I declined.Please remember: Any and all phone calls claiming to come from Microsoft or any company associated with Microsoft are scams. Don't even talk to these people! Do not give them your phone number or ANY OTHER information.
As usual I welcome comments and suggestions right here in the blog. Thank you in advance.
Stay safe.
Wednesday, September 28, 2016
Ransomware IS on the Loose, NO JOKING!
Today I met with a customer who recently I had pointed to my blog posts about ransomware. He sort of poo-pooed my words and pointed me to his safe habits.
With his permission I looked in his (very big) Inbox with about 1,000 emails. I looked only for mails with attachments and found quite a few.
I grabbed randomly one of the attachments, a ZIP file by the way, and saved that file to the computer.
Then I went to Virustotal.com, uploaded the file and had it tested. The results speak for them selves, here they are:
Clearly this file contains a downloader and a variant of the encrypting ransomware Locky. And who knows what the downloader would do to the machine if it ever gets to run.
Currently DO NOT directly open ANY attachment from an email, no matter how "good" you think you know the sender or what ever excuses your brain comes up with.
Always save the attachment to a place on your computer you can easily access like the desktop.
Then in your web browser go to virustotal.com, browse to the file - in this example on the desktop, upload the file and if virustotal.com comes up with anything then delete the file AND the email it came from!
Better safe than sorry!
And before you ask, some of my previous articles about ransomware are here, here, here, here and here.
As usual I welcome comments and suggestions right here in the blog. Thank you in advance.
Stay safe.
Labels:
HowTo,
Locky,
malware,
ransomware,
recommended,
security,
Virustotal
Tuesday, September 27, 2016
Norton Internet Security - Final Words?
Again I ran into a customer who almost insisted on keeping "his" Norton Internet Security package against my recommendation. I decided to write yet another diatribe against NIS and the reasons behind my stance.
This morning I got the current edition of a computer related newsletter that covers this very issue more concisely and better than I ever could. The text about NIS is buried in the article under the sub-heading "Why doesn’t Fred ever mention Norton/Symantec?". I want to save you the trouble of having to read (or skim) through the quite technical and lengthy discussion of file name length limitations that is the first part of the article; later in my article (what you are reading) I will quote the complete part about NIS as Fred Langa wrote it.
Who is Fred Langa? Here is the "About Fred Langa" copied directly from Windows Secrets:
Fred Langa is senior editor. His LangaList Newsletter merged with Windows Secrets on Nov. 16, 2006. Prior to that, Fred was editor of Byte Magazine (1987 to 1991) and editorial director of CMP Media (1991 to 1996), overseeing Windows Magazine and others.In short and simple words: Fred Langa is a veteran in the field of PCs and IMHO one of the most trustworthy authors about PCs out there!
Now to above mentioned quote about Norton Internet Security products. The only alteration: I shortened the name of the original questioner for obvious privacy reasons to just the initials.
Why doesn’t Fred ever mention Norton/Symantec?
P F wonders about a long-standing omission in this column.
“Is there a reason we never hear about Symantec/Norton Internet Security from Fred Langa?”
Yes, there’s a reason, Paul. The omission is quite deliberate.
I absolutely loved Norton software way back when Peter Norton was running the company. But after Symantec bought him out in the 1990’s (keeping the “Norton” name, but little else) Symantec/Norton products gained a reputation as bloated and slow; and periodically they contained extremely serious flaws.
Symantec has addressed some of the bloat problems in recent years, but shockingly severe problems still crop up.
For example, as recently as this past summer, researchers found truly frightening, flagrant flaws in all Symantec/Norton antivirus software. Some security researchers said those flaws were “as bad as it gets.”
I agree with that assessment: Due to these flaws, even an unopened email or an unclicked link could compromise your PC at its deepest level!
For more specifics, see the U.S. Government warning, “Symantec and Norton security products contain critical vulnerabilities,” the Fortune Magazine article, “Google found disastrous Symantec and Norton vulnerabilities,” and the Ghacks.net article, “Google shames Symantec for security issues.” A web search will turn up lots of other coverage, too.
Those egregious vulnerabilities were patched, but they never should have happened in the first place — especially in a nominal “security” product.
And note: That’s just one recent problem. There have been numerous other problems extending back for years. For example, I just did a general web search on ‘norton security’ problems, and found over 13 million hits!
The above are objective facts you can check for yourself. But what follows is my personal opinion:
I think running Symantec products is worse than running no security software at all. With no security software, at least you know you’re not protected. But millions of Symantec/Norton customers think the software is keeping them safe, when there’s strong evidence that it might actually be creating new vulnerabilities and system problems that wouldn’t otherwise exist. To me, that’s unconscionable in security software.
I haven’t had any Symantec products on my PCs since the early 1990s, and I don’t see that changing any time soon. I’ve seen too many problems with Symantec/Norton’s software.
Your experience might be different, and you’re certainly free to use what you like.
But now you know why you don’t see any coverage of Symantec products from me.Personally I fully and wholeheartedly agree with Fred Langa!
As usual I welcome comments and suggestions right here in the blog. Thank you in advance.
Stay safe.
Monday, September 26, 2016
Yahoo Users, it's Time to Run for the Hills
For years I have told my clients to stay away from Yahoo as far as possible. Those with Yahoo email accounts I have told to to switch their email provider.
Yes, it is a BIG hassle to do that but now it seems to be imperative to do it - finally.
Yahoo has been majorly hacked!
In 2014 already and they have kept it a secret until recently!
Reported numbers of compromised accounts vary from 500 thousand to one billion affected users but that is irrelevant; relevant is that practically all sensitive information got copied off by miscreants. User names, passwords, date-of-birth, SSNs, security questions and the answers, phone numbers, "real names", address information and the list goes on...
In California the first class action lawsuit against Yahoo has been filed and many more are expected to follow all over the nation.
What to do?
First change your Yahoo password, make the new one at least 12 characters long. Read this article from 2011(!) and this one from 2013(!) on my blog for more information.
More info on Passwords is in these articles:
Passwords that are NOT a password
Passwords the Latest
You have a Yahoo email account or use other Yahoo services (like Yahoo Financials!) and you still are "on the fence"? I can't help you, actually nobody can help you but yourself.
As usual I welcome comments and suggestions right here in the blog. Thank you in advance.
Stay safe.
Yes, it is a BIG hassle to do that but now it seems to be imperative to do it - finally.
Yahoo has been majorly hacked!
In 2014 already and they have kept it a secret until recently!
Reported numbers of compromised accounts vary from 500 thousand to one billion affected users but that is irrelevant; relevant is that practically all sensitive information got copied off by miscreants. User names, passwords, date-of-birth, SSNs, security questions and the answers, phone numbers, "real names", address information and the list goes on...
In California the first class action lawsuit against Yahoo has been filed and many more are expected to follow all over the nation.
What to do?
First change your Yahoo password, make the new one at least 12 characters long. Read this article from 2011(!) and this one from 2013(!) on my blog for more information.
More info on Passwords is in these articles:
Passwords that are NOT a password
Passwords the Latest
You have a Yahoo email account or use other Yahoo services (like Yahoo Financials!) and you still are "on the fence"? I can't help you, actually nobody can help you but yourself.
As usual I welcome comments and suggestions right here in the blog. Thank you in advance.
Stay safe.
Monday, July 25, 2016
AVG and McAfee - Not Safe
Again, please give up on so-called "security" products from AVG and McAfee.
As reported here they are not safe!
Should you not know what to replace them with then give me a call at four.one.four-seven.one.nine-two.nine.seven.seven. I look forward to hearing from you.
Stay safe!
Labels:
antivirus,
AVG,
McAfee,
security,
security suite
Monday, July 4, 2016
Norton "Security" Software - REALLY INSECURE
It is a shame that "the media" ignore these facts and thus allow millions of computer users to live with unsafe computers.
A few quotes from The Register's recent article:
- Scores (or thousands, or millions) of enterprise and home Symantec users are open to remote compromise through multiple now-patched (where possible) wormable remote code execution holes described by Google as 'as bad as it gets'.
- They [the security flaws] don’t require any user interaction, they affect the default configuration...
- Victims would not even need to open the malicious files to be compromised.
- Some of those [affected] platforms cannot be upgraded.
The other two require a level of know-how and technical expertise that is equally non-existent in the average home user environment.
The only consequent reaction for home user is what I preach to my customers for years:
Ditch any and all Norton products.If you have allowed that Norton automatically charges your credit card you have to revoke that permission. You can get their phone number(s) through this web page.
Normally uninstalling them from Programs and Features in the Control Panel is not enough. I recommend to additionally run the Norton Removal Tool downloaded from this page; click on either of the links "Download@MajorGeeks".
Stay safe.
Thursday, April 21, 2016
Windows 10 and Microsoft's Attitude to Security and Prvacy
On Slate I found this very revealing article about Windows 10 and it's implications for privacy and security. I highly recommend you read it BEFORE you jump on the Windows 10 band wagon.
No, I take back my "... highly recommend you read ...". If you are seriously thinking about Windows 10 and/or want to be fully informed before you take the plunge (or not) THE ARTICLE IS A MUST READ!
As I said in an earlier article by now we can do something about all that, reliably and free of charge. Well, maybe not totally free if you want me to set it up and demonstrate it's correct usage to you.
Stay safe!
Labels:
general,
HowTo,
Microsoft,
MS Account,
opinion,
privacy,
security,
upgrade,
Win10,
Windows 10
Wednesday, April 20, 2016
Uninstall Anything with Quick Time (or Quicktime) in the Name
Please just do it!
There is a good and free alternative player out there by the name of VLC who will happily and safely play your old .mov files - if you have any.
Stay safe!
There is a good and free alternative player out there by the name of VLC who will happily and safely play your old .mov files - if you have any.
Stay safe!
Thursday, April 7, 2016
2016-04-07 WBKV Talking Points
This is the first time ever in 12 years of regular radio shows that I do not have a set agenda for the 15 minutes ahead of us.
Listeners, please call in with ANY kind of question you may have around your PC and MS Windows.
Other than that only the standards;
- Use common sense!
- Read and think(!) before you click.
- Update ALL programs you use.
- Ransomware.
- Backup your data and your system!
And stay safe.
Labels:
general,
Gunk,
Internet,
malvertisement,
malware,
ransomware,
security,
support,
warning,
WBKV
Subscribe to:
Posts (Atom)