As far as malicious software is concerned much has changed since I last wrote about it. So here is an updated report on the current situation (summer 2014) ans my personal advice on how to stay safe on the Internet. I will talk about
- Definitions
- How to avoid these troubles and a
- Conclusion
Protective tools for the home user
Definitions:
Malware: Short for malicious software. It is a general term used to describe all viruses, worms, spyware, and pretty much anything that is specifically designed to cause harm to your PC, steal your information or throw never ending torrents of advertisements at you.
Virus: A program that copies itself and infects a PC, spreading from one file to another, and then from one PC to another when infected files are copied or shared.
Spyware: Any software that collects your information without your knowledge and usually sends that information back to the creator(s) so they can use that personal information in some nefarious way.
Scareware: A relatively new type of attack, where a user is tricked into downloading what appears to be an antivirus application, which then proceeds to tell you that your PC is infected with hundreds of viruses, and can only be cleaned if you pay for a full license. Of course, these scareware applications are nothing more than malware that holds your PC hostage until you pay for the “full” version. In many cases you can't uninstall them and/or the render the PC unusable.
Trojan horses: Applications that look like they are doing something innocuous, but secretly have malicious code that does something else. In many cases, trojans will create a backdoor that allows your PC to be remotely controlled, either directly or as part of a botnet—a network of computers also infected with this trojan and/or other malicious software. The major difference between a virus and a Trojan is that trojans don't replicate themselves—they must be installed by an unwitting user.
A computer worm uses a network to send copies of itself to other PCs, usually utilizing a security hole to travel from one computer to the next, often automatically without user intervention and often via email.
Ransomware usually encrypts your files that then are useless to you and some even “lock” your computer. The software requests an often quite substantial payment for the means to restore your files into usable form – which even after payment sometimes fails.
Protective tools for the home user
You will always want to run a specialized anti virus program and a specialized on-demand only malware removal tool. I will recommend the only two programs I have learned to trust over the years – and that are easy enough to handle for the home user.
Anti virus: The release of Microsoft Security Essentials has changed the landscape of antivirus software. We finally have a completely free application that protects against viruses, spyware, and other malware without killing system performance like some of the "suites" tend to do. In my extensive personal experience it barely slows down even relatively slow machines and it's user interface is the easiest to use of all I know.
Don't only take my word for it. AV-Test.org found that it detects 98% of their enormous malware database and AV-Comparatives (a widely known anti-malware testing group) found that MSE was one of only three products that did well at both finding and removing malware.
Anti malware: Modern malware, mostly called PuP (potentially unwanted program), is very different from classic viruses. Most anti-virus programs can not detect PuPs and thus do nothing about it. And, as if to add insult to injury, most of them come on the computer because the user got tricked into allowing their installation.
I recommend Malwarebytes Anti-Malware (MBAM for short). Please download it from these two links only (they both go to the same destination).
MBAM is a time proven product and available in a totally sufficient free version. You have to watch during the original install and when you install a program update. The last window of the installer looks like this:
MBAM is a time proven product and available in a totally sufficient free version. You have to watch during the original install and when you install a program update. The last window of the installer looks like this:
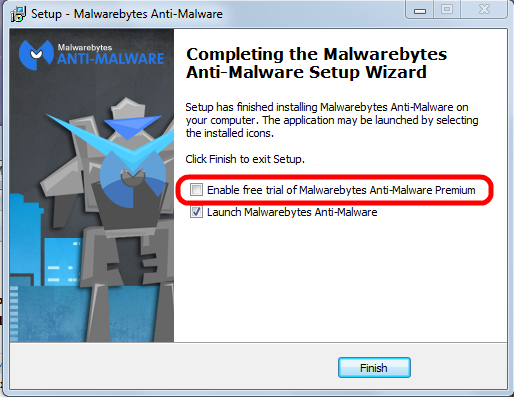
Please pay attention to the marked entry; it's check box is preselected! That means the “trial version” will be activated and after the trial period ends you would have to pay for using the program.
You have to uncheck this check mark.
Eventually the program itself needs to be updated; the installer will run again and again you have to pay attention to this little detail to avoid the for-pay version!
See this article on how to correctly use MBAM.
See this article on how to correctly use MBAM.
How to avoid all these troubles
When it comes to protecting yourself, it's laughable how many people install multiple antivirus applications but don't keep their system updated with the latest patches for the operating system.
If everybody would simply keep their system and all programs up to date, we wouldn't have to worry so much about these problems. If the constant rebooting action of Windows Update has you frustrated, you can always temporarily delay the reboot; remember, only after the reboot the patches are completely installed and active to protect your computer..
Keeping your applications updated is critically important to protect your computer's security. Your firewall won't protect you, and an antivirus software is unlikely to help if you're using an old, vulnerable version of Adobe Flash or Adobe Reader.
Conclusion
In the end, good browsing habits and common sense should be your first line of defense against any kind of malware. I recommend to always run a good security suite like MSE and additionally to use MBAM as an on-demand scanner. That way you're as well protected as easily possible and you can scan your system for malware whenever you want.
So here's the bottom line: In my not so insignificant experience MSE and the on-demand free version MBAM work very well together . Coupled with good browsing habits and common sense this a good combination of security tools and judiciously using them should keep you well protected.
As usual I welcome comments and suggestions right here in the blog. Thank you in advance.
Click here for a categorized Table Of Contents.
Click here for a categorized Table Of Contents.

No comments:
Post a Comment