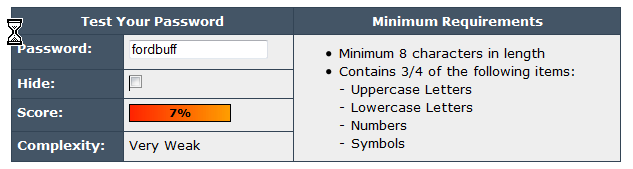
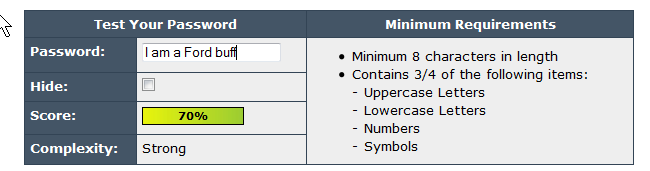
I got this email from a customer:
. . . I heard on the news today that Google is one of many companies whose computers were recently hacked and that passwords were obtained. I don’t use Google mail on my computer but rather Windows mail. However, in order to have access to Play Store apps, I had to open a Google account on my Samsung smartphone and that password is the same as my computer password. I just closed my Google account on my smartphone. Should I change my password on my computer and if so, how do I do that? I use that same password extensively for other applications. . .
Here is my reply:
You raise a heck of a lot of important questions in your text. Because the issues you are touching on
IMHO are very important I will try to reply to every single part separately and interspersed in your text.
I heard on the news today that Google is one of many companies whose computers were recently hacked and that passwords were obtained.
A good example of uninformed sensationalist reporting. What literally ALL halfway decent companies stores are NOT passwords but
encrypted passwords. That is technically and for hacking purposes a BIG difference.
I don’t use Google mail on my computer but rather Windows mail.
IMHO using ANY Microsoft email program puts your computer at a far greater risk that the stolen Passwords do. "only" two million passwords from together three companies were stolen; these affected companies together have many
hundreds of millions of users. That makes the percentage of compromised passwords VERY small.
There were no reports on how these passwords got in the wrong hands. I have no information on this either but I suspect that some gang of miscreants had a well working virus program on many computers world wide and that virus program copied the passwords. Now
THAT would be bad because the virus program would get the real and not yet encrypted passwords directly from the keyboard when they are typed.
Update 12/09.1023: I just read that it was actually
154 million accounts that got compromised. Now That's a different thing now.
However, in order to have access to Play Store apps, I had to open a Google account on my Samsung smartphone and that password is the same as my computer password.
1. Exactly what do you mean with "computer password"? The one you type to log on to your Windows account or one that you use on any web site? The former is no problem, just change it locally on your computer. The latter poses possibly a risk.
2. Using the same password on more than one service is always a risk and should be avoided.
I just closed my Google account on my smartphone.
That does not eliminate risks from stolen passwords.
Should I change my password on my computer and if so, how do I do that?
That depends on what exactly the password is used for that you mention. If it is for your local user account then google the name of your operating system and change the password; google something like "windows 7 change user password". You will get many pages with descriptions of how to do that.
I use that same password extensively for other applications. . .
That definitely is about the biggest mistake you can make. Please read the following articles on my blog for lots of background information:
Passwords too simple and what to do about it.
Hacked Passwords deals mainly with email issues.
Passwords that are NOT a password
Passwords the Latest
Especially the last article above has all the nitty gritty. Follow the link in "The article I read is
here ". There you find all the technical background you could possibly want.
Update 12/09.2013: Hackers often like to publish their discoveries, and the databases
of hacked, stolen passwords were uploaded for all to see. This allowed
the people behind a rather useful website to create a searchable copy of
the list, so that you can check whether your details appear on a list
of some 154 million stolen online accounts and email addresses.
To find out whether your details do indeed appear on any of those stolen lists, just head to
http://www.haveibeenpwned.com/ and
type in your email address on the home page. If that address is among
any of the lists of stolen accounts, you'll be warned straight away.
Above two paragraphs are a literal copy from
here.
I hope this long reply helps in addition to giving you a lot of information and confusion. Please keep asking.
As usual I welcome comments and suggestions right here in the blog. Thank you in advance.
Stay safe!