Wednesday, December 28, 2016
How I Transfer Files From An Old To A New Computer
As long as the "old" computer is basically still working transferring all your user files (documents, pictures, music and videos) is no issue at all as long as they are stored in Windows' standard locations.
After the new computer is up and running I take the disk drive physically out of the old machine, attach it externally to the new machine and copy the files directly across to the new computer.
This way there is only one copy process which saves time compared to copying via an external drive which requires copying the same data twice.
After copying the files to the new machine I will urge you to safely keep the disk drive from the old computer for at least a year as an insurance against data loss.
Imagine you need a certain file after several months, you know the name of the file but it just is not where you thought it should be. It is on the old disk drive because that is the only place files could have gotten stored on the old machine; so that is where we have to search for it.
I hope that clears eventual confusion.
Stay safe.
Labels:
file transfer,
general,
HDD,
new computer,
recommended,
support
Sunday, December 18, 2016
Still on Yahoo? Time to RUN!
Are you still using Yahoo! ® ?
It is high time you run, fast, far and NOW!
Just read this article by Rob Schifren. He is the driving force and creator of TechSupportAlert.com, a very long running and very reliable source of information about free software and many more things about and around computers; computers used here in the widest sense of the word, that is including Apple Mac, Android devices and much more.
From the many contacts with my customers I have an idea about how many people re-use the same password on several (or all) web sites.
PLEASE heed the warning and AT LEAST establish a new STRONG password for your Yahoo account.
IMHO it would be better if you switched to a different service altogether. If you have and use a Yahoo email account I recommend to switch to Gmail.
Gmail can automatically import emails from Yahoo if you want to give your email contacts time to adapt to your new email address.
As usual I welcome comments and suggestions right here in the blog. Thank you in advance.
Stay safe.
Thursday, November 24, 2016
About Scams - Beware!
It saddens mw but it has to be said again and again:
Microsoft WILL NOT CALL you because your computer "has been reported" or anything similar.Please take the few minutes to read this article from the How-To-Geek on common scamming tricks and what to do about them. This article talks about some other commonly encountered scams as well, not only the Microsoft or Tech Support based scams.
It always is good to be well informed. The time to read the HTG article is time well spent; it can help you to avoid the most common traps.
Stay safe.
Monday, November 21, 2016
NO to Google Chrome - Here is Why
Here is a quote from this article on The Register:
Why would a person want to willingly live with more risks than less?
This seems to me to be a good time to talk about the most common argument for Google Chrome, at least as far as I hear from my customers. The argument is "Yeah, but Chrome is faster". Mostly I get that from younger people or grandparents who quote family members or friends thereof.
That argument is "true" only to a laughably small effect that IMHO is totally irrelevant.
Every web page is made up of often numerous files; these files have to be transferred from the server computer of that web page into our computer. The time this transfer takes is solely dictated by the real life speed and performance of our Internet connection. Our computer and the web browser have next to no influence on that transfer.
Only after all the files that comprise the web page are on our computer the web browser can begin to build the visible web page on the screen. Yes, in doing this Google Chrome is faster than other browsers but this is maybe 10% of the total time it takes from us clicking on a link to the web page appearing on our screen.
Let me do the math for an extremely slow example: Assumed it takes 10 seconds from click to visible page (which is quite long!). 90% of this time is waiting for the transfer of the file(s), that is 9 out of 10 seconds; only 10% (equals 1 second) is what the browser takes to actually do it's job of giving us something to look at. Even if Google Chrome were 20% faster than another browser that would amount to being 0.2 seconds faster over all. That difference is well below what humans can perceive!
My point is: "Faster" is by no means "better"!
As usual I welcome comments and suggestions right here in the blog. Thank you in advance.
Stay safe.
Chrome leads the browser pack with 504 reported vulnerabilities followed by Internet Explorer with 289 and Firefox with 171. Some 1035 flaws were reported across all browsers including Opera and Safari, up from 728 in 2013."Reported vulnerabilities" are in layman's terms known weaknesses in the program code of the web browser that have been or could eventually be used to hack through a given web browser into computers.
Why would a person want to willingly live with more risks than less?
This seems to me to be a good time to talk about the most common argument for Google Chrome, at least as far as I hear from my customers. The argument is "Yeah, but Chrome is faster". Mostly I get that from younger people or grandparents who quote family members or friends thereof.
That argument is "true" only to a laughably small effect that IMHO is totally irrelevant.
Every web page is made up of often numerous files; these files have to be transferred from the server computer of that web page into our computer. The time this transfer takes is solely dictated by the real life speed and performance of our Internet connection. Our computer and the web browser have next to no influence on that transfer.
Only after all the files that comprise the web page are on our computer the web browser can begin to build the visible web page on the screen. Yes, in doing this Google Chrome is faster than other browsers but this is maybe 10% of the total time it takes from us clicking on a link to the web page appearing on our screen.
Let me do the math for an extremely slow example: Assumed it takes 10 seconds from click to visible page (which is quite long!). 90% of this time is waiting for the transfer of the file(s), that is 9 out of 10 seconds; only 10% (equals 1 second) is what the browser takes to actually do it's job of giving us something to look at. Even if Google Chrome were 20% faster than another browser that would amount to being 0.2 seconds faster over all. That difference is well below what humans can perceive!
My point is: "Faster" is by no means "better"!
As usual I welcome comments and suggestions right here in the blog. Thank you in advance.
Stay safe.
Tuesday, October 4, 2016
The newest Scam - Beware
The newest telephone scam I heard of is the Microsoft Licensing Scam. You may get a phone call or a voice mail saying something like this (phone numbers deliberately obscured):
“This is to notify you that your Microsoft Windows license key has been expired in your computer so Microsoft Corporation has stopped the services in your computer. To renew the Windows license key, please call 866 XXX XXXX. Let me repeat. This is to notify you that your Microsoft Windows license key has been expired in your computer so Microsoft Corporation has stopped the services in your computer. To renew the Windows license key, please call 866 XXX XXXX. I will repeat 866 XXX XXXX.”The message obviously was from a computer generated, sort of "mechanical" voice and the stilted English suggest a non-native English speaker behind the whole thing.
Any messages about licensing issues truly from Microsoft would pop up on your computer's screen only during installation or activation. And we all know, if only from experience, that a Microsoft license for the Operating System comes with the computer when you buy it and it is good for the lifetime of the machine.
In Windows services are programs running in the background; they are required for even basic functions of the computer. A computer would not work at all without the required services running in the background.
In the case I read about the recipient happened to be a very, very experienced Windows user; the gentleman called back the 866 number from the message; he said about that call:
"Because the number was toll free, I called it just to see what would happen. An answering machine invited me to leave a message and my number for a callback — I declined.Please remember: Any and all phone calls claiming to come from Microsoft or any company associated with Microsoft are scams. Don't even talk to these people! Do not give them your phone number or ANY OTHER information.
As usual I welcome comments and suggestions right here in the blog. Thank you in advance.
Stay safe.
Wednesday, September 28, 2016
Ransomware IS on the Loose, NO JOKING!
Today I met with a customer who recently I had pointed to my blog posts about ransomware. He sort of poo-pooed my words and pointed me to his safe habits.
With his permission I looked in his (very big) Inbox with about 1,000 emails. I looked only for mails with attachments and found quite a few.
I grabbed randomly one of the attachments, a ZIP file by the way, and saved that file to the computer.
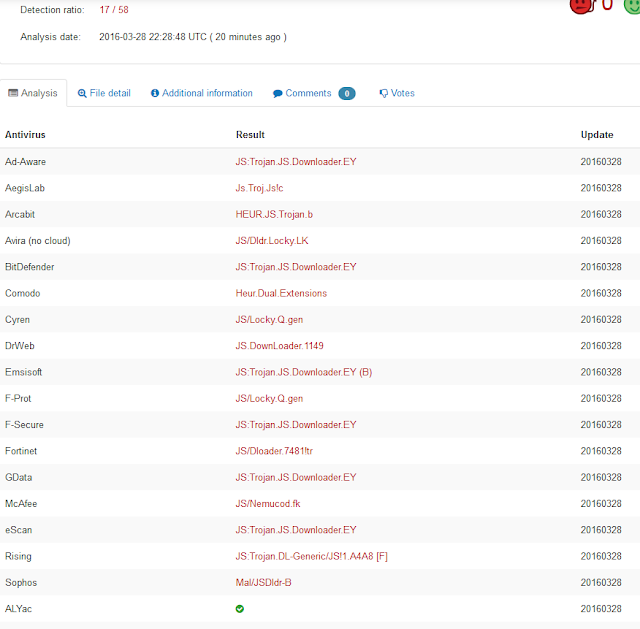
Then I went to Virustotal.com, uploaded the file and had it tested. The results speak for them selves, here they are:
Clearly this file contains a downloader and a variant of the encrypting ransomware Locky. And who knows what the downloader would do to the machine if it ever gets to run.
Currently DO NOT directly open ANY attachment from an email, no matter how "good" you think you know the sender or what ever excuses your brain comes up with.
Always save the attachment to a place on your computer you can easily access like the desktop.
Then in your web browser go to virustotal.com, browse to the file - in this example on the desktop, upload the file and if virustotal.com comes up with anything then delete the file AND the email it came from!
Better safe than sorry!
And before you ask, some of my previous articles about ransomware are here, here, here, here and here.
As usual I welcome comments and suggestions right here in the blog. Thank you in advance.
Stay safe.
Labels:
HowTo,
Locky,
malware,
ransomware,
recommended,
security,
Virustotal
Tuesday, September 27, 2016
Norton Internet Security - Final Words?
Again I ran into a customer who almost insisted on keeping "his" Norton Internet Security package against my recommendation. I decided to write yet another diatribe against NIS and the reasons behind my stance.
This morning I got the current edition of a computer related newsletter that covers this very issue more concisely and better than I ever could. The text about NIS is buried in the article under the sub-heading "Why doesn’t Fred ever mention Norton/Symantec?". I want to save you the trouble of having to read (or skim) through the quite technical and lengthy discussion of file name length limitations that is the first part of the article; later in my article (what you are reading) I will quote the complete part about NIS as Fred Langa wrote it.
Who is Fred Langa? Here is the "About Fred Langa" copied directly from Windows Secrets:
Fred Langa is senior editor. His LangaList Newsletter merged with Windows Secrets on Nov. 16, 2006. Prior to that, Fred was editor of Byte Magazine (1987 to 1991) and editorial director of CMP Media (1991 to 1996), overseeing Windows Magazine and others.In short and simple words: Fred Langa is a veteran in the field of PCs and IMHO one of the most trustworthy authors about PCs out there!
Now to above mentioned quote about Norton Internet Security products. The only alteration: I shortened the name of the original questioner for obvious privacy reasons to just the initials.
Why doesn’t Fred ever mention Norton/Symantec?
P F wonders about a long-standing omission in this column.
“Is there a reason we never hear about Symantec/Norton Internet Security from Fred Langa?”
Yes, there’s a reason, Paul. The omission is quite deliberate.
I absolutely loved Norton software way back when Peter Norton was running the company. But after Symantec bought him out in the 1990’s (keeping the “Norton” name, but little else) Symantec/Norton products gained a reputation as bloated and slow; and periodically they contained extremely serious flaws.
Symantec has addressed some of the bloat problems in recent years, but shockingly severe problems still crop up.
For example, as recently as this past summer, researchers found truly frightening, flagrant flaws in all Symantec/Norton antivirus software. Some security researchers said those flaws were “as bad as it gets.”
I agree with that assessment: Due to these flaws, even an unopened email or an unclicked link could compromise your PC at its deepest level!
For more specifics, see the U.S. Government warning, “Symantec and Norton security products contain critical vulnerabilities,” the Fortune Magazine article, “Google found disastrous Symantec and Norton vulnerabilities,” and the Ghacks.net article, “Google shames Symantec for security issues.” A web search will turn up lots of other coverage, too.
Those egregious vulnerabilities were patched, but they never should have happened in the first place — especially in a nominal “security” product.
And note: That’s just one recent problem. There have been numerous other problems extending back for years. For example, I just did a general web search on ‘norton security’ problems, and found over 13 million hits!
The above are objective facts you can check for yourself. But what follows is my personal opinion:
I think running Symantec products is worse than running no security software at all. With no security software, at least you know you’re not protected. But millions of Symantec/Norton customers think the software is keeping them safe, when there’s strong evidence that it might actually be creating new vulnerabilities and system problems that wouldn’t otherwise exist. To me, that’s unconscionable in security software.
I haven’t had any Symantec products on my PCs since the early 1990s, and I don’t see that changing any time soon. I’ve seen too many problems with Symantec/Norton’s software.
Your experience might be different, and you’re certainly free to use what you like.
But now you know why you don’t see any coverage of Symantec products from me.Personally I fully and wholeheartedly agree with Fred Langa!
As usual I welcome comments and suggestions right here in the blog. Thank you in advance.
Stay safe.
Monday, September 26, 2016
Yahoo Users, it's Time to Run for the Hills
For years I have told my clients to stay away from Yahoo as far as possible. Those with Yahoo email accounts I have told to to switch their email provider.
Yes, it is a BIG hassle to do that but now it seems to be imperative to do it - finally.
Yahoo has been majorly hacked!
In 2014 already and they have kept it a secret until recently!
Reported numbers of compromised accounts vary from 500 thousand to one billion affected users but that is irrelevant; relevant is that practically all sensitive information got copied off by miscreants. User names, passwords, date-of-birth, SSNs, security questions and the answers, phone numbers, "real names", address information and the list goes on...
In California the first class action lawsuit against Yahoo has been filed and many more are expected to follow all over the nation.
What to do?
First change your Yahoo password, make the new one at least 12 characters long. Read this article from 2011(!) and this one from 2013(!) on my blog for more information.
More info on Passwords is in these articles:
Passwords that are NOT a password
Passwords the Latest
You have a Yahoo email account or use other Yahoo services (like Yahoo Financials!) and you still are "on the fence"? I can't help you, actually nobody can help you but yourself.
As usual I welcome comments and suggestions right here in the blog. Thank you in advance.
Stay safe.
Yes, it is a BIG hassle to do that but now it seems to be imperative to do it - finally.
Yahoo has been majorly hacked!
In 2014 already and they have kept it a secret until recently!
Reported numbers of compromised accounts vary from 500 thousand to one billion affected users but that is irrelevant; relevant is that practically all sensitive information got copied off by miscreants. User names, passwords, date-of-birth, SSNs, security questions and the answers, phone numbers, "real names", address information and the list goes on...
In California the first class action lawsuit against Yahoo has been filed and many more are expected to follow all over the nation.
What to do?
First change your Yahoo password, make the new one at least 12 characters long. Read this article from 2011(!) and this one from 2013(!) on my blog for more information.
More info on Passwords is in these articles:
Passwords that are NOT a password
Passwords the Latest
You have a Yahoo email account or use other Yahoo services (like Yahoo Financials!) and you still are "on the fence"? I can't help you, actually nobody can help you but yourself.
As usual I welcome comments and suggestions right here in the blog. Thank you in advance.
Stay safe.
Monday, July 25, 2016
AVG and McAfee - Not Safe
Again, please give up on so-called "security" products from AVG and McAfee.
As reported here they are not safe!
Should you not know what to replace them with then give me a call at four.one.four-seven.one.nine-two.nine.seven.seven. I look forward to hearing from you.
Stay safe!
Labels:
antivirus,
AVG,
McAfee,
security,
security suite
Saturday, July 23, 2016
What browser?
I got an email from a customer and believe my reply might be of interest to many people. The customer quoted an article from another blog(?) that recommended to search directly out of the URL field. Here is my reply verbatim as I sent it:
The crux with all these "easy" tips is that they all play right into the industry's game.
The more searches any given search engine gets to perform the more money they can ask for their aggregated info on what we search for. The search engine companies may not directly advertise to us but the companies that buy this aggregated search information can then advertise better and more directly to us.
- It's a fact that Bing and Yahoo (they use Bing) do NOT show us what in the search results are paid advertisements.
- It's a fact that way too many advertisements get abused to get malicious programs on our computers.
- It's a fact that some web browsers (like IE and Edge, both from Microsoft!) make it very difficult or don't allow us at all to suppress advertisements.
- It's a fact that Google does not allow us to suppress certain advertisements in Google's own Chrome browser.
All the before said and more is behind my STRONG recommendation to use only Firefox as I set it up for my customers.
And I urge my customers to search ONLY out of the little browser specific Search window:
because when you search from there you get a Google search resultStay safe!
MINUS any advertisement(s),
PLUS the red, yellow and green Web of Trust ratings right by every search result.
AND your search with Google has happened anonymously!
Update Jan. 10th 2017:
Sadly around November 5th 2016 Mozilla, the organization that supplies Firefox and Google have removed that piece of code from their download pages; some details are here.
If you remove the WOT extension or add-on from your Firefox browser it currently can not be re-installed!
Google recently made the WOT extension available again.If that is not reason enough for any of my customers it's their decision and their money if I have to clean up their machine again.
Monday, July 4, 2016
Norton "Security" Software - REALLY INSECURE
It is a shame that "the media" ignore these facts and thus allow millions of computer users to live with unsafe computers.
A few quotes from The Register's recent article:
- Scores (or thousands, or millions) of enterprise and home Symantec users are open to remote compromise through multiple now-patched (where possible) wormable remote code execution holes described by Google as 'as bad as it gets'.
- They [the security flaws] don’t require any user interaction, they affect the default configuration...
- Victims would not even need to open the malicious files to be compromised.
- Some of those [affected] platforms cannot be upgraded.
The other two require a level of know-how and technical expertise that is equally non-existent in the average home user environment.
The only consequent reaction for home user is what I preach to my customers for years:
Ditch any and all Norton products.If you have allowed that Norton automatically charges your credit card you have to revoke that permission. You can get their phone number(s) through this web page.
Normally uninstalling them from Programs and Features in the Control Panel is not enough. I recommend to additionally run the Norton Removal Tool downloaded from this page; click on either of the links "Download@MajorGeeks".
Stay safe.
Wednesday, June 22, 2016
Using a Computer with a Visual Impairment
My recent personal experience with AMD and a close relative being cured from almost blindness due to massive cataracts have left me with greater awareness of the problems around vision loss.
And surprisingly just very recently a blind customer of mine sent me an email regarding using computers with a vision impairment; thank you Li Su. I believe this information may be very important so I will quote the relevant text of the email here.
Disclaimer: I can in no way guarantee the accuracy and/or the contents of the following information; I rely on the qualification of it's source.
Stay safe.
-----
Using a Computer with a Visual Impairment: A Beginner's Guide to Computer Accessibility
By Bill Holton
Computer Access for People Who Are Blind or Have Low Vision
Findings from the 2012 National Health Interview Survey (NHIS) Preliminary Report established that an estimated 20.6 million adult Americans (or nearly 10% of all adult Americans) reported they either "have trouble" seeing, even when wearing glasses or contact lenses, or that they are blind or unable to see at all.
Of course if you (or a loved one) have recently experienced profound vision loss, these numbers are little more than mere statistics. We mention them here for one reason: to assure you that you are not alone. Vast resources—human, technical, medical, and rehabilitative—stand ready to assist you in regaining your independence, resuming your career or starting a new one, and, most importantly, increasing your enjoyment of life, friends, and family.
In this section we will focus on the technical resources that are available to those with visual impairments. We’ll begin by describing one of the most profound technological achievements to have benefited sight-impaired individuals: the accessible personal computer.
This guide is organized into two main sections. The first section is for those with new visual impairments who are brand new to computers
The second section is for those with recent visual impairment who already own, and have some experience using, a personal computer
Related Links
·Helpful Products and Technology for Living with Vision Loss
-----
Sunday, May 22, 2016
"Force Feeding" Windows 10
"Force Feeding" are the only words adequate to describe what Microsoft is doing right now! My email inbox is overflowing with complaints and cries for help. Microsoft seems to be really desperate, it must not be going as well as they had hoped.
After the upgrade to Windows 10 (not update) you have 4 weeks to revert to your previous system. This process has so far worked without a hitch for those of my customers who reverted.
- Click the Start button
- Click on Settings (on a few systems it is PC Settings)
- Click on Update & security
- In the left side bar click on Recovery
- Find the entry Go back to Windows x (x is 7 or 8 depending on what your previous system was) and click on it
Microsoft has since about November 2015 been busy to put some of the telemetry of Windows 10 into Windows 7 and Windows 8 systems; this happens in addition to forcing upgrades to Windows 10. That means that Win 7 and 8 systems now contain some of what I call Windows 10 spying on me/us and IMHO that should to be turned off!!
My recommendation is to turn all this junk off and luckily since about February 2016 I know of a dependable piece of free software that allows everybody to do just that on their systems whether it is a Windows 7, 8 or 10 computer!. See this article for more details.
If after the upgrade any icons or programs are missing or if you rather have me install SD Anti Beacon I can do all that via remote support. For remote support please call one of the coming Monday through Thursday evenings between 6PM and 8PM. If I am already at home I want to connect remotely to your computer. If I can not answer on your first attempt please assume that I am already helping somebody else and keep trying every 10 or 15 minutes.
If I have set up or worked on your computer during the last three years you should be set for remote support; if you have an icon labeled either "Teamviewer ..." or "EJH Remote Support" then all is prepared. If you do not find either of these icons please call anyway, I can walk you on the phone thru the steps to get the remote support program going. Alternatively you can prepare for remote support as described here.
Please have your computer up and running; if your computer is a notebook (or laptop) computer then please have the power supply connected and plugged into a working power outlet.
Stay safe!
Labels:
AntiBeacon,
general,
HowTo,
Microsoft,
privacy,
rant,
recommended,
Spybot,
support,
upgrade,
Win10,
Windows 10
Thursday, April 21, 2016
Windows 10 and Microsoft's Attitude to Security and Prvacy
On Slate I found this very revealing article about Windows 10 and it's implications for privacy and security. I highly recommend you read it BEFORE you jump on the Windows 10 band wagon.
No, I take back my "... highly recommend you read ...". If you are seriously thinking about Windows 10 and/or want to be fully informed before you take the plunge (or not) THE ARTICLE IS A MUST READ!
As I said in an earlier article by now we can do something about all that, reliably and free of charge. Well, maybe not totally free if you want me to set it up and demonstrate it's correct usage to you.
Stay safe!
Labels:
general,
HowTo,
Microsoft,
MS Account,
opinion,
privacy,
security,
upgrade,
Win10,
Windows 10
Wednesday, April 20, 2016
Uninstall Anything with Quick Time (or Quicktime) in the Name
Please just do it!
There is a good and free alternative player out there by the name of VLC who will happily and safely play your old .mov files - if you have any.
Stay safe!
There is a good and free alternative player out there by the name of VLC who will happily and safely play your old .mov files - if you have any.
Stay safe!
Thursday, April 7, 2016
2016-04-07 WBKV Talking Points
This is the first time ever in 12 years of regular radio shows that I do not have a set agenda for the 15 minutes ahead of us.
Listeners, please call in with ANY kind of question you may have around your PC and MS Windows.
Other than that only the standards;
- Use common sense!
- Read and think(!) before you click.
- Update ALL programs you use.
- Ransomware.
- Backup your data and your system!
And stay safe.
Labels:
general,
Gunk,
Internet,
malvertisement,
malware,
ransomware,
security,
support,
warning,
WBKV
Tuesday, March 29, 2016
Avoid or Mitigate Ransomware Risks
A big THANK YOU to the Emerging Threats Team at SophosLabs and their blog Naked Security for their excellent recommendations on this nasty but important topic.
I have taken the liberty to add some remarks just to help you remember important little details that are easy to forget in cursive.
- Backup regularly and keep a recent backup copy off-site.
There are dozens of ways other than ransomware that files can suddenly
vanish, such as fire, flood, theft, a dropped laptop or even an
accidental delete. Encrypt your backup and you won’t have to worry about
the backup device falling into the wrong hands.
But do not, I repeat, do not leave your backup device connected to the computer. Always unplug the backup device after the backup is complete!
- Don’t enable macros in document attachments received via email.
Microsoft deliberately turned off auto-execution of macros by default
many years ago as a security measure. A lot of malware infections rely
on persuading you to turn macros back on, so don’t do it!
Naturally they don't tell you that the click they ask you to do will turn macros back on. They rather trick you into believing that clicking is the thing to do to be able to read what they sent you...
- Be cautious about unsolicited attachments.
The crooks are relying on the dilemma that you shouldn’t open a document
until you are sure it’s the one you want, but you can’t tell if it’s the one
you want until you open it. If in doubt, leave it out.
Currently I do not open ANY attachments; I call the sender and have them explain what and why they sent the attachment and even if all that checks out I additionally check the attachment on Virus Total.
- Don’t give yourself more login power than you need. Most importantly, don’t stay logged in
as an administrator any longer than is strictly necessary, and avoid
browsing, opening documents or other “regular work” activities while you
have administrator rights.
Quite a lofty ideal as I am currently experiencing first hand.
- Consider installing the Microsoft Office viewers. These viewer applications
let you see what documents look like without opening them in Word or
Excel itself. In particular, the viewer software doesn’t support macros
at all, so you can’t enable macros by mistake!
Now is a good suggestion, I will have to do that!
- Patch early, patch often. Malware that
doesn’t come in via document macros often relies on security bugs in
popular applications, including Office, your browser, Flash and more.
The sooner you patch, the fewer open holes remain for the crooks to
exploit.
As I always preach: Update, update, update.
Stay safe!
Labels:
attachment,
Backup,
email,
general,
HowTo,
malware,
ransomware,
recommended,
security,
Virustotal
Monday, March 28, 2016
Ransomware - A Current Example
Please take a close look at this cut out grabbed diectly off my screen:
From the top the red frames are around:
- The virus infected scam email in the message list
- The totally unprofessionally empty subject line.
[Bulk] is from my ISP telling me that this email was sent from a server that is known to send out spam
FW: tells me that the email was forwarded - Addressing me with "ejheinze" shows that the sender does not even know my first name;
ejheinze is the part of my email address before the @ character - A totally unprofessional signature
- .zip is one of the potentially dangerous file types
- Hm, no subject and I don't know a Jodie M and Comcast in her email address? I have no business at all with Comcast.
- Unprofessional and bordering on rude.
- Totally unprofessional and in a primitive way impolite.
- From Comcast I would at least expect some sort of company logo or an avatar.
- I wonder what might be in there...
but with all the above I DO NOT CLICK on the attachment!
The rest was simple:
Delete the email which deletes the attachment as well.
Delete the file from the computer and
Empty Recycle Bin, just to be sure.
Remember: NEVER, EVER click on an email attachment unless you have verified it's legitimacy with the sender.
Stay safe.
Labels:
email,
general,
netiquette,
pup,
ransomware,
thunderbird,
virus,
Virustotal
Sunday, March 27, 2016
Spybot Anti Beacon - A Must Have?
If privacy of your data and files is to you as important as it is for me than the answer to the title question on Windows 7 and above is YES, clear and loud.
Let me explain: SpyBot Anti Beacon is a relatively new utility that can reliably turn off most of Windows 10's unwelcome behavior. Many others besides myself think of as being spied at. Whether Micro$oft calls this telemetry or whatever, I feel spied at.
If you want to know why I call Windows 10 a masterpiece of data collection and judge it's telemetry as for me unwanted spying please read this article originally written in October 2012 after Windows 8 was available. And I repeated the IMHO main reason in the context of Windows 10 quite recently.
If you want to try SB Anti Beacon (SBAB) please keep in mind this is professionally made but it is a FREE program; free as in free beer, that is you do not have to pay for it. This has consequences; not everything is as automatic as you might have come to expect from good programs. The main program window has four tabs for four different functions or info screens. I recommend to read the Frequently Asked Questions in tab #4 but will shortly describe what I do in tabs #1 and #2 (usage instructions).
In tab #1 I want ALL the entries to be green, that is all the spying turned off. So I just click the Immunize button at the bottom of the page.
In tab #2 I want as well all entries to be turned off but the page is differently organized. For every entry I have to click on the Apply button immediately above the entry. And especially on laptops and other (mainly smaller) wide screens I have to realize that in tab #2 the program windows has a scroll bar! I need to use it to uncover the last entry or entries on that tab's page.
Here are some visual examples from the only Windows 10 system I currently have available which happens to be a laptop:
Tab #1 BEFORE and AFTER "Immunize"
Tab #2 BEFORE and AFTER "Apply"
Just an hour ago I made an interesting observation: After installing updates from Windows Update I checked the Win 7 system I write this on and there was one new telemetry entry in each of the tabs. That shows that Micro$oft at least for now will keep bringing telemetry from Windows 10 back to Windows 7 and 8!
That is why I say to you: If you are willing to use SpyBot's Anti Beacon and to take on this additional check after EVERY update from Micro$oft (whether the updates were automatically applied or you checked and installed them manually) then you can rest fairly assured that Micro$oft will not collect data from your computer and about your computing habits.
As usual, stay safe.
Labels:
AntiBeacon,
general,
privacy,
recommended,
security,
Spybot,
support,
warning,
Win10,
Windows 10,
Windows 8,
Windows 8.1,
Windows7
Wednesday, March 23, 2016
2016-03-24 WBKV Talking Points
Today nothing but viruses, malware and currently acute dangers.
- Ransomware (so far mainly from infectious MS-Office documents)
Record ransom paid; 17 million US$
- - - now infectious advertisements on BIG company web sites with 100s of millions of visitors every day:
- -
New York Times (nyt.com)
AOL.com
ESPN.com
MSN.com (MicroSoft Network)
NFL.com (yes, National Football League)
TheWeatherNetwork.com
TheHill.com
Yahoo.com and many more.
If you see advertisements in your web browser your computer is at risk!
Firefox web browser with Adblock Plus and WOT are the browser protections you should use!
No, not Goggle Chrome, Safari or Edge or Internet Explorer!
Monday, March 21, 2016
Norton Software IS RISKY!
For years I recommend to my customers and on my radio shows to stay away from so called "security products" from the big names like Norton, McAfee, Trend Micro and many others.
The makers of the Norton branded software is a company called Symantec.
Here is revealing and interesting article about Symantec and some of the major security problems in some of their software.
If you want to entrust the security of your computer to Norton software be my guest. I don't mind at all to clean up the mess.
Stay safe!
Labels:
general,
McAfee,
Norton,
security,
security suite,
Symantec,
Trend Micro,
warning
Credit cards ARE a risk factor...
.., especially if last year you used them at Target or Home Depot.
Home Depot so far shelled out $19.5 million and they are still counting.
More details are here.
Personally I always cringe when I see someone paying everyday smaller mounts with a credit card, be it at Starbucks, McDonald or anywhere else.
Disclaimer: I am hardly ever at McDonald and if at all I pay with cash!
Stay safe!
New Dangers And Bad News
You may already have heard of ransomware, the newest trick of the bad guys to get at your money.
If you have not here is a VERY SHORT explanation: A ransomware virus encrypts all your data files, that is in effect makes them unusable and unreadable. After the encryption is done you have to pay money to the crooks do get instructions and a "decryption key"; if the instructions and the decryption key work correctly as they should you get your data back but sometimes it does not work. Your data is held for ransom, hence the name.
So far the highest amount reportedly paid by a large California based medical organization was 17 million dollars.
Very recently the web sites of a whole lot of well known and big organizations got abused to show advertisements infected with ransomware. Some of the affected web sites were:
- msn.com
- nytimes.com
- aol.com
- nfl.com
- theweathernetwork.com
- thehill.com
- zerohedge.com
I can not say it often and loud enough:
If you see advertisements on the Internet your web browser and thus your computer are NOT SAFE at all! Fire your current technician and call me or send me an email!When I leave a customer's house they ALL have a safely set up web browser that should not show ANY of these commercially distributed advertisements.
Stay safe.
Labels:
ad-blocker,
adblocker,
encryption,
general,
malvertisement,
malvertising,
ransomware,
virus,
warning
Saturday, March 19, 2016
Skype Users Be Warned
If you use Skype PLEASE read through this article about two conversations triggered by Skype friend requests. I will let that speak for itself.
For the less geeky of my readers, a spam bot is program or robot programmed to "have a conversation".
You are warned.
Stay safe.
Wednesday, March 9, 2016
2016-03-10 WBKV Talking Points
Part 2: Stay Safe on the Internet
Be aware that trustworthy companies, especially Microsoft and it’s affiliates, will never contact you because of a supposed technical problem of any kind.
The following will definitely be scams: - Phone calls
- Advertisements for technical support for any software product on search engines like Google, Yahoo or Bing
- Pop-ups for tech support from social web sites (Facebook! or LinkedIn)
- Pop-ups for tech support that promote phone based tech; these usually require a previous malware infection or an unsafe web browser.
- Never completely trust someone you don’t know who called you.
Listen to them, if you like.
- Ask questions, if you feel like it, but NEVER EVER give them access to your PC
- NEVER EVER give them any payment information.
- Tell them that you will let your local tech look into it (even if you don’t have one).
- If the caller hangs up – good for you.
- If he/she gets impolite or abusive it’s your time to hang up!
Chances are there’s nothing to see at all.
If you have handed over payment information, you’ve just given that information to a complete stranger. Immediately put your credit card or payment provider on fraud alert. If you allowed the scammer to access your computer things can get ugly. Do NOT use the computer; you usually have no idea what they did. You need a trusted technician to check out your machine.
This IS a common scam right now and the best defense is to not fall for it in the first place.
Another currently growing threat: MS-Word, Excel or Powerpoint files sent as attachments! When these files are opened you mostly see the request “... to turn protection on ...” or similar tricks. Don’t do it, don't believe it, it's a trick! Many very nasty ransomware viruses use this trick! If you do not have a current backup YOU PAY! You either pay the crooks to get your files back and/or a trusted technician to re-build all the software on your computer. And if you don't have install disks for Windows - b.t.w. they do NOT come with computers any longer - you have even more problems.
Stay safe.
Wrong, Every Step She Took Wrong
Original text of email I got from a long ago customer:
Recently our Microsoft Essentials "little house" has been erratic in its stability. We have done full scans and quick scans with it staying green for a short period of time changing to orange and then eventually to red.And here is the original text of my reply, please judge for yourself:
I googled this question and received an answer that Microsoft is not updating this since last year - so the definitions are not really up to date. Is this true?
It was suggested that I get AVG Anti Virus which is Free. I did do this and it appears to be doing the job with the green circles, etc.
On that same page there is a area where I can check to "fix performance". It is a PC Analyzer - After doing this, the report was: many errors in various areas and they said it could be fixed for fee/one time and/or I could get a program for 1 year. I would not need one for one year but I would like take advantage of the free analyzing of this performance. Do you think I should do this and is AVG a good solution if indeed Microsoft has stopped updating?
... [I] realize we will have to update to windows 10 when they force us to do so. If we do not do this will they charge us?
Thanks for asking. If you remember I do not express myself politically correct so please brace yourself for some rough truths:
I believe I still could fix the situation and hopefully repair your computer. I guarantee that the free solution will not work to your satisfaction.
- The "little house" you refer to represents Microsoft Security Essentials which was your anti virus program until you installed AVG.
- ANY anomaly with your anti virus should have rang a LOUD alarm bell.
- If it has not updated since last year your computer potentially was not protected against common viruses.
- AVG is a program that I urge my customers to stay away from!
- It installs really crappy programs, that is how AVG (the company) makes money nowadays.
- PC Analyzer IMHO is known malware.
- I bet you that almost ALL the errors that you get shown are false messages meant to scare you into installing even more useless programs.
- Keep going with these silly suggestions and soon your computer will likely not be usable any longer.
- No, DO NOT take "advantage" of the "free" solution that you mention, it will make it only worse.
The question about "they" ( I assume you mean Microsoft?) charging you only Microsoft can answer and they, MS, has been asked the same thing thousands of times; so far MS has only replied with marketing blah-blah; we just do not know. My personal suspicion is yes, no later than January 2020 when in MS's view Windows 7 comes to the end of it's supported lifetime.
In case my replies offended you I apologize, that was and is not my intention at all.For my readers here: No further comment from my side; please come to your own conclusion and PLEASE, don't make similar or the same mistakes.
Stay safe.
Wednesday, February 24, 2016
2016-02-25 WBKV Talking Points
Stay Safe on the Internet
-
Always install Operating System updates
-
Keep your installed applications up-to-date
-
Do not use the same password at every site
-
Install and be sure to update your anti-virus software
-
Additionally install a free anti-malware scanner and use it(!) regularly
-
Use a firewall (the FW built-in to Windows is good enough!)
-
Backup your data!
-
Enable the display of file extensions
-
Do not open attachments from people you do not know (especially Word files, Locky ransomware travels in Word files! Use MS's Word and Powerpoint viewers to check files)
-
Delete emails that say you won a contest or a stranger asking for assistance with their inheritance or money transfer
-
Watch out for online and phone support scams
-
Ignore and close web pop ups saying your computer is infected or has a problem (use ALT+F4)
-
Ignore and close web pop ups that pretend to be a Windows alert (use ALT+F4)
-
Some types of web sites are more dangerous than others
-
Be extra vigilant when using Peer-To-Peer Software (torrents!)
-
When installing software, watch for "bundled" tool bars and programs you don't want
-
Read the End User License Agreement (EULA) Lol, I know!
Sunday, February 21, 2016
Windows 10 and why I change my recommendation
On 1/17/2014 I wrote on this blog a rant titled: Microsoft Accounts and Windows 8 – A Rant
For Windows 10 this article is just as valid today. I want to quote the main point (emphasis added):
Apple has made an incredible fortune "having access" to all this information about their customers and as I see it Microsoft wants to bake themselves a similar pie, not only get a slice [of this pie of advertisement money]. Once I realized this my reaction was "Big Brother. . . ".IMHO Windows 10 is a masterpiece of a copy of that pie, even with some improvements; it's main objective is to gather information about and from the user; why else would Microsoft assign a unique "advertising ID" to every email address that unsuspecting users give them?
As often in this life where there is light there is shadow and vice versa. And besides the "shadow" that I call outright spying there is light:
Technically Windows 10 is a really good operating system.
The main complaints can by now be alleviated with third party programs.
- The data reporting can reliably be turned off (no more spying!) while the helpful reporting about the inner workings of the system (or failures to do so) remains active.
- The main menu can look and feel just like your old version of Windows; it can look and
work just like you were used to from Windows Vista or Windows 7.
But be warned: When you upgrade to Windows 10 IMHO you have to install and correctly configure the program that turns Windows 10's reporting features OFF! And do NOT give Microsoft your email address, it will be treated as a Microsoft account!
Again, if privacy is of any concern to you then DO NOT give Microsoft your email address! That includes that you should NOT use Skype! We have a free alternatives to Skype that does not require to give your email address to Microsoft.
Remember what I wrote in Windows 10 Settings - What I Recommend (August 8th. 2015):
If you gave the system on first start your email address Microsoft has created on their servers the storage for an immense wealth of information about you that Win10 and it's programs will collect from and about you; and that besides the fact that every email address will have it's unique "advertisement ID" assigned. Guess what that will be used for!
Should you feel asked a bit too much with all this please contact me by email, I can help. An email address to contact me is in non-computer readable format at the end of the Welcome paragraph in the left side bar of my blog.
And if you upgraded and don't like what you see you have four weeks to 30 days (conflicting info from MS!) to revert back to what you had before.
Stay safe.
Labels:
general,
Microsoft,
upgrade,
Vista,
Win10,
Windows 10,
Windows 8,
Windows 8.1,
Windows7,
WindowsXP
Wednesday, February 10, 2016
2016-02-11 WBKV Talking Points
Today I want to talk only (or mainly) about modern malware and how it gets in our computers.
Pull up this web page and you have the detailed blueprint for today's talk.
The 10 worst offenders are (IMHO #1 is by far the worst one):
- Download portals
- Fake updates (e.g. Java, Adobe Flash, Yahoo!)
- Installer programs (mainly from download portals)
- PuPs downloading and installing more PuPs
- Express installation (expressway to an infected computer)
- Custom Install abused with confusing EULAs
- Home page and search provider changed
- Forced install (e.g. Inbox Toolbar)
- Other people(!) using your computer (visitors, relatives)
- Researching PuPs; do it ONLY in a virtual machine!
Saturday, February 6, 2016
Windows 10 Now FORCED On Your Computer
You have good reasons to stay with Windows 7 or Windows 8.1? If the world were like Microsoft wants it to be you are out of luck, plain and simple.
Since this month Microsoft, true to what they announced in November last year, will only give you a choice to "Upgrade Now" or to "Upgrade later".
There is NO WAY to decline the upgrade, neither only for now or for the future as well. Now, I admit, the latter was wishful thinking anyway.
Since most of my customers call themselves computer illiterate I recommend to stay away from registry editing or similar DIY solutions.
The only comprehensive, user friendly and dependable solution I know of is GWX Control Panel.
Warning: Do NOT click on the title "GWX Control Panel", the name of this program; this would start the download immediately!
Instead I recommend you read through the description and then read the detailed description of how to use the program and of what the program does. Read this even if you don't fully understand all technical details; it will give you a comprehensive overview and make using the program far easier.
After reading these descriptions you should go back to the first page I linked you to above. To the right of the description of GWX Control Panel are two download links, one for an Installer version and one for the Stand-alone version. I prefer the Stand-alone version because installer programs IMHO introduce an unnecessary additional layer of complexity.
I leave it up to you to decide which version you want to download and use.
Stay safe.
Labels:
GWX Control Panel,
Microsoft,
upgrade,
Win10,
Windows 10
Top 10 Ways PUPs Sneak Onto Your Computer. And How To Avoid Them.
Disclaimer: I copied the title literally from this blog post.
And that is all I want to say here; this article is simply a MUST READ if you ever had PuPs installed or had to call me because everything got so slow or whatever problem you had.
95% or more of all computer problems I encounter nowadays are initially caused by a PuP! The authors of these PuPs have gotten very clever and constantly invent new tricks to dupe the unsuspecting computer user.
Only permanent vigilance, caution and attention to detail can ultimately somewhat protect us and our computers.
Please note the use of the word "somewhat" in the previous paragraph!
For the first time ever I will directly recommend a piece of commercial security software.
If you want the IMHO best automatic protection against all kinds of malicious programs including PuPs then you will have to pay some money, currently just shy of $40 per year for a single computer. You find details about Emsisoft Anti-Malware here.
Another disclaimer: I am in no way at all associated with Emsisoft or any of their distributors or resellers!
If you don't want to pay that is fine, you just have to DIY (do it yourself). MSE or Defender in conjunction with Malwarebytes Free will do it just as well but you have to regularly do more yourself.
Whether you want to pay for Emsisoft Anti-Malware or not doesn't really matter, IMHO you simply HAVE TO READ this article.
Stay safe.
Labels:
Ad-Aware,
ad-blocker,
adblocker,
Ant-Malware,
cleanup,
crapware,
deception,
Emsisoft,
general,
Gunk,
Internet,
malvertisement,
malware,
Malwarebytes,
portals,
security,
support,
warning
Wednesday, January 27, 2016
2016-01-28 WBKV Talking Points
Through 20 years of effort, we have successfully trained every
computer user
to use passwords that are hard for humans to remember,
but easy for computers to guess.
to use passwords that are hard for humans to remember,
but easy for computers to guess.
10
most used passwords in 2015 (truly a list of shame!):
123456
password
12345678
qwerty
12345
123456789
football
1234
1234567
baseball
password
12345678
qwerty
12345
123456789
football
1234
1234567
baseball
Please,
in the interest of privacy and safety, use a password
manager and let it create long
passwords.
Wifatch
virus actively protects its
victims from other forms of malware;
It infects routers, not computers;
It infects routers, not computers;
It is written in the Perl programming language
It targets so far only ARM (83%), MIPS (10%), and SH4 (7%) processors
It connects infected devices to a peer-to-peer network
It targets so far only ARM (83%), MIPS (10%), and SH4 (7%) processors
It connects infected devices to a peer-to-peer network
Basically
it only infects devices that are not protected at all
in the first place!
A Symantec
(Norton) partner company in
India uncovered as major player in
the all too common technical support scam.
Security
Suites from AVG and Avast install dangerous browser
add-ons!
McAfee and Norton tell
Windows 10 users that they better use Internet Explorer, a browser so
bad that Microsoft gave up on it!
For years I advise against ALL
of the well known “security suites”, free or paid versions, no
difference.
Labels:
general,
McAfee,
Microsoft,
Norton,
password,
Radio show,
security,
security suite,
Symantec,
WBKV
"Free" Security programs - For A Price
I stumbled over this article on How-To-Geek.
I wan to save you the hassle and time to read this lengthy article your self and will quote a few selected and IMHO most relevant snippets.
My stance toward the remaining "free" security programs as well as the well known commercial offerings is known; I have expressed this here repeatedly. So let's begin:
Don't despair, a good, time proven free solution is available since about 2009.
For now over 13 years I "fix" my customer's home computers by removing all sorts of viruses and other malicious or obnoxious software. Most of my customers call themselves "computer illiterate". All of them have lived safely with mostly little or no manual effort.
The only malware infections happen now when someone "falls" for a social engineering trick; that is in effect when the customer for a moment was inattentive. And hat is just a human weakness, I know from my very own experience.
If you want to know details about this solution plese drop me a personal email; thank you.
I wan to save you the hassle and time to read this lengthy article your self and will quote a few selected and IMHO most relevant snippets.
My stance toward the remaining "free" security programs as well as the well known commercial offerings is known; I have expressed this here repeatedly. So let's begin:
- Free antivirus applications aren’t what they used to be. Free antivirus
companies are now bundling adware, spyware, toolbars, and other junk to
make a quick buck.... At one point, free antivirus was just advertising, pushing users to
upgrade to the paid products. Now, free antivirus companies are making
money through advertising, tracking, and junkware installations.
- Comodo ... change[s] your web browser’s search engine to Yahoo! and
bundles the GeekBuddy paid tech support software. It also bundles other
Comodo products you might not want, including changing your DNS server
settings to Comodo’s servers and installing “Chromodo,” a Chromium-based
browser made by Comodo. ... As the Comodo-affiliated PrivDog software contained a massive security hole similar to the one Superfish had, there’s a good chance you don’t want a bunch of other Comodo-developed software and services thrown onto your computer.
- Lavasoft’s Ad-Aware pushes “Web Protection” that will “secure your
online search” by setting SecureSearch as your web browser’s homepage
and default search engine. Despite the name, this isn’t actually a
security feature. Instead, it just switches your web browser to use a
branded search engine that actually uses Yahoo! in the background — this
means it’s powered by Bing.
If you prefer Bing, that’s fine — just use the full Bing website. You’ll have a better experience than using Lavasoft’s rebranded, stripped-down search engine.
- Avira encourages you to install “Avira SafeSearch Plus.” This is just a
rebranded version of the Ask Toolbar, redirecting your search results
through a rebranded version of Ask.com’s search engine. If you wouldn’t
want the Ask Toolbar installed, you wouldn’t want this rebranded version
of it installed either.
- ZoneAlarm also wants you to enable “ZoneAlarm Search” as your browser’s
default homepage and search engine, along with installing a ZoneAlarm
toolbar that is - once again - a rebranded version of the Ask Toolbar.
- Panda {Free Antivirus] attempts to install their own browser security toolbar as well as
change your browser’s search engine to Yahoo, and its home page to
“MyStart,” which is powered by Yahoo. To Panda’s credit, they at least
don’t attempt to trick you by offering you a renamed Yahoo search engine
or home page.
- avast!’s installer also tries to install additional software you
might not want. We’ve seen Dropbox offered here in the past, but avast!
attempted to install the Google Toolbar when we tried installing it.
Programs like the Google Toolbar and Dropbox are high-quality software you might actually want, so avast! comes out looking very good compared to the other options here. But even avast! has done done some questionable things in the past — witness the avast! browser extension inserting itself into your online shopping.
-
AVG has its own suite of obnoxious utilities, including the AVG Security Toolbar, AVG Rewards, AVG Web TuneUp, and SecureSearch.
- BitDefender offers a stripped-down free antivirus. ... BitDefender is still pursuing the strategy of attempting to upsell you to the paid product.
- MalwareBytes doesn’t attempt to install any extra junk on your
computer, although the free version doesn’t offer real-time protection.
To their credit, MalwareBytes is offering a free tool that’s useful for
manual scans - it even picks up and detects [and removes!] much of the adware other
programs install - and encouraging you to pay for a more full-featured
product.
This tool could be quite useful in combination with another antivirus, like Microsoft’s free Windows Defender or Microsoft Security Essentials solution. But it’s not a standalone free antivirus you can depend on, as it lacks the real-time scanning.
Don't despair, a good, time proven free solution is available since about 2009.
For now over 13 years I "fix" my customer's home computers by removing all sorts of viruses and other malicious or obnoxious software. Most of my customers call themselves "computer illiterate". All of them have lived safely with mostly little or no manual effort.
The only malware infections happen now when someone "falls" for a social engineering trick; that is in effect when the customer for a moment was inattentive. And hat is just a human weakness, I know from my very own experience.
If you want to know details about this solution plese drop me a personal email; thank you.
Wednesday, January 13, 2016
2016-01-14 WBKV Talking Points
For the normal home user: Upgrade
to Windows 10 will be enforced by January!
Only two ways around:
1. Change Windows Update Settings. Not recommended because permanent user involvement required.
2. Use GWX Control Panel. See my blog Jan. 3rd. 2016
Only two ways around:
1. Change Windows Update Settings. Not recommended because permanent user involvement required.
2. Use GWX Control Panel. See my blog Jan. 3rd. 2016
AVG
installs an extension in Google Chrome that opens computers to
malware. DO NOT use Google
Chrome and/or AVG “security products! See my blog Jan. 3rd.
2016
First
ransomware
written in Java discovered. Please uninstall
all Java.
To my knowledge only Pogo.com still offers games written in Java.
Using
Internet Explorer version 10 or older? Update
it now! Support runs out NOW!
Better: Finally make the switch to Mozilla Firefox browser.
Better: Finally make the switch to Mozilla Firefox browser.
And a very recent true horror story about Dell's technical support
and their willingness to handle a warranty case.
Labels:
Dell,
general,
Microsoft,
Radio show,
ransomware,
security,
WBKV,
Windows 10
Sunday, January 3, 2016
How to avoid Windows 10
Are you tired of Microsoft's permanent nagging to upgrade to Windows 10?
Do you want to avoid the computer world's biggest and most openly staged attempt to get the greatest data collection system world-wide set up?
Then here is THE solution - as far as I know and as of January 3rd 2016.
Download GWX Control Panel from this web page. I recommend to use the portable version called "Stand-alone" and please read the program author's user guide.
You best start GWX Control Panel [GWXcpl] in administrator mode, that means you right click on the program file and the click on "Run as administrator".
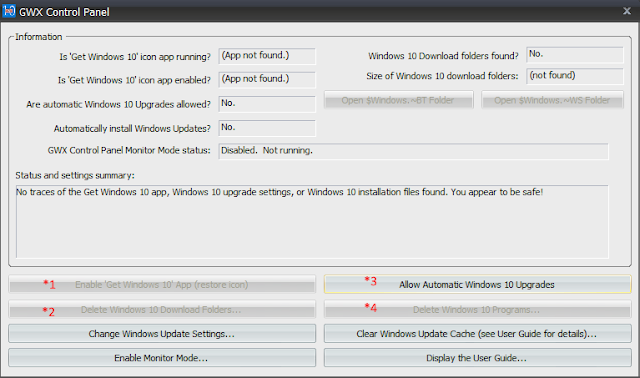
The GWXcpl windows looks like similar to this:
I can not show you an EXACT picture because I have no computer that is still unprotected from Windows 10 upgrades.
On your computer the upper part will have different contents; I believe it is very self explanatory.
In the lower part you will probably see instead of *n these text entries:
*1 Disable 'Get Windows 10 App' ...I recommend to at least click on Disable "Get Windows 10 App' ..." and on "Prevent Automatic Windows 10 Upgrades". Whether you want to delete Windows 10 files and/or folders is up to you; on older computers with less than 320GB large disk drives it seems to be a good idea to free up the space. And don't forget to reboot when you are asked to even if it means that you may have to run GWXcpl more than once.
*2 Delete Windows 10 Download Folders
*3 Prevent Automatic Windows 10 Upgrades
*4 Delete Windows 10 Programs
Feel free to ask any uestions you might have, preferably by email.
Stay safe.
Labels:
cleanup,
deception,
download,
GWX Control Panel,
GWXcpl,
HowTo,
Microsoft,
recommended,
security,
upgrade,
Win10,
Windows 10
AVG + Google Chrome = TROUBLE
Happy and healthy New Year to everybody!
... It's the first post in 2016 ...
The title describes the newest formula for disaster.
For years I have advised against using Google Chrome as your primary web browser.
For years I have advised against using AVG's free "security" programs.
Now this combination has become a wide open barn door for malicious software and/or viruses to take over your computer. You can read more about the details here.
If you use AVG I recommend to uninstall it and instead rely on Microsoft's Defender respectively Security Essentials in Windows 7. If you run into problems when you uninstall AVG you find AVG's special removal programs here. Take care to download the correct "bittedness" version for your version of Windows.
I you use Google Chrome I recommend to install Mozilla's Firefox browser; in Firefox you need to install two extensions or add-ons:
That plus some applied common sense is all you need to be and stay safe on the Internet.
If you want to do more against eventual advertisement malware and so called PUPs then download THE FREE version from here. Install Malwarebytes only AFTER you read this article about how to install and use it correctly.
Stay safe!
... It's the first post in 2016 ...
The title describes the newest formula for disaster.
For years I have advised against using Google Chrome as your primary web browser.
For years I have advised against using AVG's free "security" programs.
Now this combination has become a wide open barn door for malicious software and/or viruses to take over your computer. You can read more about the details here.
If you use AVG I recommend to uninstall it and instead rely on Microsoft's Defender respectively Security Essentials in Windows 7. If you run into problems when you uninstall AVG you find AVG's special removal programs here. Take care to download the correct "bittedness" version for your version of Windows.
I you use Google Chrome I recommend to install Mozilla's Firefox browser; in Firefox you need to install two extensions or add-ons:
- Adblock Plus and
- WOT (Web Of Trust)
That plus some applied common sense is all you need to be and stay safe on the Internet.
If you want to do more against eventual advertisement malware and so called PUPs then download THE FREE version from here. Install Malwarebytes only AFTER you read this article about how to install and use it correctly.
Stay safe!
Labels:
ad-blocker,
adblocker,
AVG,
download,
Google Chrome,
HowTo,
malware,
Malwarebytes,
MBAM,
MSE,
pup,
security
Subscribe to:
Posts (Atom)