Computers and everything around them change at quite a
rapid pace. Especially the Internet is ever changing and with it the threats
are changing that we encounter. The crooks that want to use our computers to
their own advantage are adapting faster to changes in computer technology and
on the Internet than most users even become aware of the changed environment.
The changes in Operating systems from Windows XP to Windows
7 are so significant that some common viruses from 2002 through 2006 just could
not survive in a Windows 7 environment. Naturally the crooks are very aware of
that and they have adapted their software and their ways to get malicious
programs running on your computer.
Although it would still get your computer infected nowadays
you don’t have to go to “iffy” web sites anymore; you don’t need to download
illegally copied music, movies or license keys for expensive games. Your
computer can get badly infected without
you even going to a danger zone.
Today one of the major avenues chosen by crooks are
advertisements. One simple remedy is to follow this rule:
Do NOT click on or in any advertisement.
Especially if the ad promises a “free gift” or claims you
have been chosen as a “winner”. Trust me: Nobody gives an Apple iPad 2 or a
modern smartphone away for free!
If you think that web sites or services you use daily like
Google, web based email (Gmail, Hotmail, Yahoo mail, MSN mail and the like) or
even Facebook ought to be “safe” then you better think again.
For example so called product recommendations that seem to
come from a Facebook friend most likely are infected advertisements; they will
nail your computer with malicious software.
Sometimes that malicious stuff is
so nasty that we would have to rebuild the whole system from scratch – which
means you’d lose everything
currently stored on your computer’s disk drive.
The art of writing malicious software is not as much
technical skill to write a self-replicating virus program anymore as it has
become the art of social engineering. By
now you can buy “proven to work” virus code from the Internet, you just have to
do the social engineering to get the victim to click or to watch the
advertisement or to play that seemingly innocuous little video. Some examples of social engineering tricks are:
- Making a supposed headline sufficiently
salacious to entice you to “click to read more”.
- Promising a “win” in some unnamed lottery.
- Promising coveted gadgets; currently an Apple
iPad, Apple iPhone 4S or an Android smartphone do the trick.
- Promising something about “wardrobe
malfunctions” or the like; sex sells, you know?
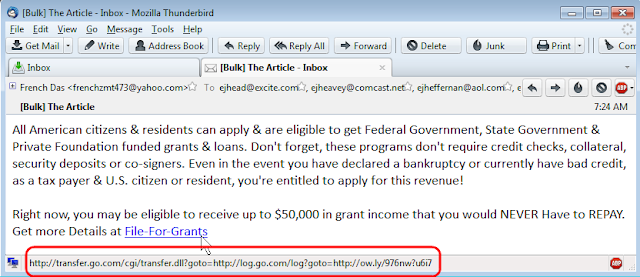
- Claiming a package could not be delivered and
promising to show you the order or even the invoice for the contents of the
package.
- Plenty of other tricks, too many to list here.
What happens when you inadvertently click on the
wrong link or ad? Most likely your computer gets infected with a program from a
wide selection of nasty pieces of
malware. Some examples are:
- Trojan
Horse programs sitting secretly on your computer and enabling their creators
to use your computer for their purposes.
- Scareware
programs that claim to have detected dozens of viruses; if you fall for the
scare
- you will be directly out of some money,
- you will have given your credit card information
to some crook or
- you most likely will have “bought” a program that
will be really bad and hard to remove.
- Key
Loggers that will record all your keystrokes, all login names, all
passwords, all account numbers and so on.
- Bots (short
for Robots), hidden programs that can do and be used for absolutely anything illegal or criminal. Bot
activity has brought the FBI to quite a few houses of unsuspecting people.
It
has become quite difficult to always stay clear of these dangers.
So what can we do?
- Read this
article on my blog and cover the basics.
- Use Mozilla Firefox as your web browser; just
by doing this you eliminate a large percentage of malicious programs and
attacks.
- If you use an email
program use Mozilla Thunderbird instead of any Microsoft email program; by doing this you eliminate a large percentage of email borne risks and attacks.
- Install the Adblock Plus extension in Firefox
and Thunderbird. Correctly installed ABP will block all advertisements from known commercial advertisement
servers!
- Use a dependable ant virus program. Currently I
strongly favor Microsoft Security Essentials. You can read about the “why”
here,
here,
here
and here.
Did I forget something important? Please leave a comment
below, I will reply here as well.
As usual I welcome comments and suggestions right here in
the blog. Thank you in advance.